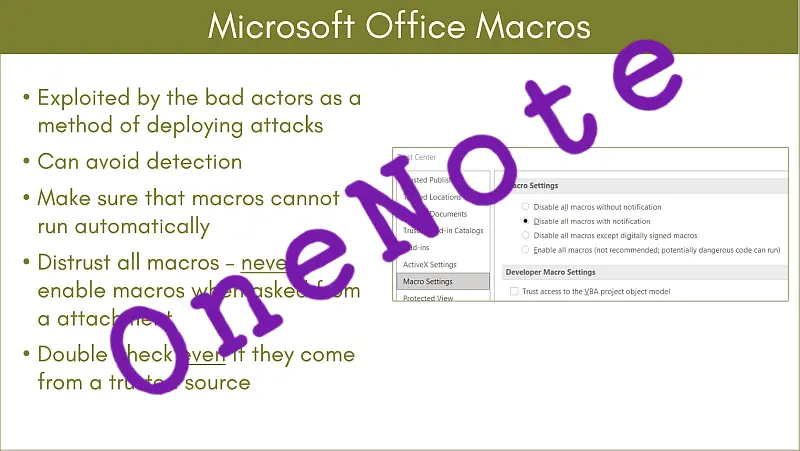
Once it had been discovered how straightforward it is to obscure a malicious package inside a OneNote .one attachment and mixed with “something new”, that users may not have seen before, it was obvious that the use of .one attachments for the delivery of malware was going to go up.
Now the prolific malware Emotet – malware that steals information for future email phishing campaigns and can download and activate other malicious packages – is the latest malware to exploit OneNote:
Emotet malware now distributed in Microsoft OneNote files to evade defenses (bleepingcomputer.com)
OneNote comes with Windows 10 and Microsoft 365 but from my experience is not not widely used – your experience may differ – but when I mention that I use OneNote widely, it is my universal app across my mix of Microsoft, Apple and Linux devices, often I get the response that they do not use OneNote. Too complicated! What does it do for me?
So now you have a widely distributed software package and a user base that is not very aware of the product. Even if they use OneNote they are probably unaware of the .one extension, it is not obvious when using the product. A good mix if you are looking for a way to get your malware past the defences, with the added bonus that you may get a curious “clicker” who just wants to see what a .one file is!
Your take away from this, is make sure you and your team are aware of the rogue ,one attachments doing the rounds in malicious phishing emails.
Sadly, you just need one user to accidentally allow a malicious file to run for an entire corporate network to be compromised in a full blown ransomware attack.
Lawrence Abrams, Bleeping Computer
Have a look at our training – it will help.
Clive Catton MSc (Cyber Security) – by-line and other articles
Further Reading