As you probably know, if you follow this blog, I was in Edinburgh last week at the 6th Intl. Conference on Big Data, Cybersecurity & Critical Infrastructure held at the Craiglockhart Campus, Edinburgh Napier University. For my post this week I wanted to share one positive thing I got from the speakers so here it is – “realistic cyber security”.
What does realistic cyber security mean?
Cyber security professionals, including me, spend a lot of time and column inches discussing tools, attacks, procedures and many other “cyber security things” but Rory Alsop (he is the CISO and Head of Cyber Security for Tesco Bank) had a definition for cyber security that moved away from the things.
Here is his slide:
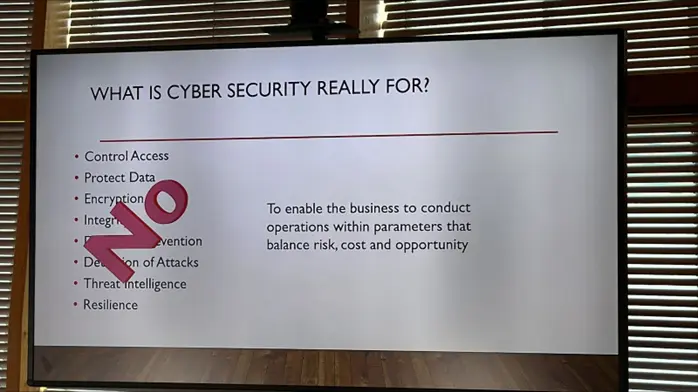
So what realistic cyber security is, is what your organisation needs to continue functioning in a world where cyber security threats are real, having looked at the risks you face, the chance of those things happening and the budget you have available.
Simple.
But the threat landscape is always changing
Becky Pinkard (she is the MD of Global Cyber Operations for Barclays) had a great slide showing the expanding threat landscape forward to 2030.

This is the threat landscape that your realistic cyber security has to face.
Realistic cyber security – what can you do?
Becky had something to say on this. She thought that a well informed and trained team would lead to a supportive culture that would help combat this growing cyber security threat. These are things that we often write about here and on CyberAwake as they are really important. Becky also thought that monitoring of the organisation’s systems coupled with threat intelligence and cyber security analysis would support your team and build your culture.
That is what she works towards at Barclays.
But Barclays and Tesco have “loads of money”
They do and so they can afford an extensive array of cyber defences. But the increase of the threat landscape has caused a filtering down of very effective tools to even the smallest of organisations – maybe like your own.
We can offer training, help you examine your risks, write you a report on your current business resilience etc. We can also supply managed endpoint protection and monitoring software. But one of the most exciting things we have is affordable continuous 24/7 monitoring complete with cyber security analysts ready to implement instant incident response if you need it. And if they jump – you need it.
We are already meeting with clients about this service ahead of its imminent launch.
Artificial Intelligence
Of course the conference included the threat and promise of artificial intelligence and we will be coming back to it. But as a taster, the image at the top of the page is of Professor Bill Buchanan – he headed up the course I took at Napier University, demonstrating the use of ChatGPT in crafting the perfect social engineering messages and inflating his CV!
Clive Catton MSc (Cyber Security) – by-line and other articles
Further Reading
Cybersecurity in the Spotlight as Edinburgh Napier’s Innovation Hub hosts flagship Global Cyber Conference – Research Innovation Enterprise (I am not sure how long this link will last)
Email Phishing is a constantly changing threat
Although not everything was great!
Photo credits https://www.clivecatton.co.uk/


