Today we are going to look at the very first meeting I have with clients where we look at risk analysis. This is not a blog about eating an elephant – that is a figure of speech – although I do have a book that includes a paragraph or two on how to prepare elephant! (Dodwell. 1986).
This is just a roundabout way to say that nearly every client I talk to is a little bit intimidated when it comes to starting a cyber security project. It was a difficult meeting I had last week and a difficult meeting I need to have this week.
Risk Analysis – Forget about the Size
Risk analisys is the place to start, it begins to inform everyone where the challenges for the cyber security project will be and where the money needs to be spent. To get around the size of the project I use a whiteboard (or in the case of the example below a projector-connected iPad and OneNote* ) and put up a few headings to get the discussion going. For instance:
Contractors – Data – Equipment – Networks – Organisation – People – Sites – Software
I then ask for suggestions from the room… then I start to create a diagram similar to below.
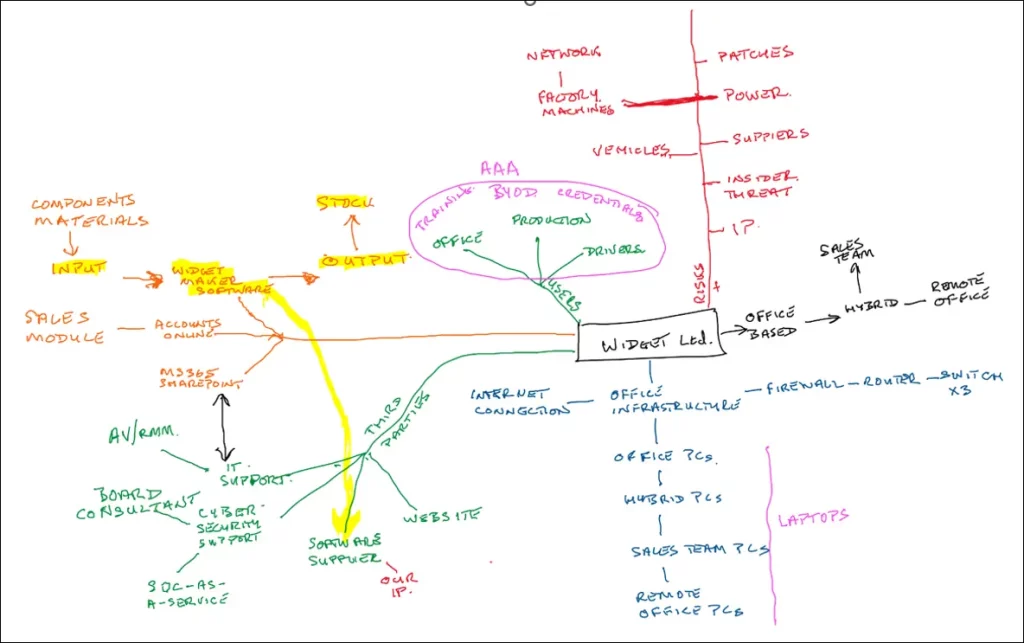
Notice that the headings are not on the diagram. I do not want people to be led into answers by me – I want the work to reflect their organisation, operation, and risks.
With this diagram comes scope…
This diagram is obviously not real – apologies to Widget Ltd if you exist – I cannot share a real one with you. However, my example gives you an idea of how, when taking on a huge project where most people do not know where to start, I get it onto a whiteboard so we can work on it.
Who is in the room?
It needs to be anyone who can contribute to an understanding of what the organisation is actually doing. It is decided in a meeting before we ever sit down and be prepared to discover that you need someone who is not there.
Risk Analysis – Just a start…
I was not planning to take you through the whole process – it takes time. What I want you to take away from this article is “do not ignore doing something about your cyber security because you cannot see the edges of the project”.
Clive Catton MSc (Cyber Security) – by-line and other articles
* You should try using an iPad, an Apple Pencil and OneNote for this exercise. It gives a much bigger canvas than a whiteboard and when combined with zooming can create very informative, detailed diagrams. Subsequent notes and diagrams can be linked inside OneNote and to external resources. Then the whole lot or just relevant pages can be shared across the risk analysis team.
And as a bonus you can encrypt those notes and diagrams that need it.
You guessed it I like OneNote.
References
Dodwell, C. (1986). An Explorer’s Handbook: An Unconventional Guide for Travelers to Remote Regions. Facts on File.
Photo by ThisIsEngineering


