I am out of the office this week and that is why I am going to reproduce an article here, that I wrote last year for CyberAwake about the “Out-of-Office” automatic reply.
The Out-of-Office Email and How it Compromises Your Organisation’s Cyber Security
Before heading out on our leave, we all use that handy feature in our email – the Out-of-Office (OOO) auto-reply notification. There is that fear that a vital email will be missed, a sale not made, a client offended, if they do not get a reply. However, there are cyber security and risk considerations before you let your people announce to anyone who emails them, that they are not around.
So how does that compromise your cyber security? You are just being polite.
If you give threat actors any extra information they will use it against you. What the crooks are looking for is something to persuade you to click on that link (Lawson, Zielinska, Pearson and Mayhorn. 2017).
But surely the hackers are not watching me?
You’re right, they are not watching you – probably. But an automated “regular” phishing email, that initiates an OOO, can start a process of investigation that can lead to a targeted phishing attack.
So what does that mean for me?
One of the things we regularly do during the Cyber Security Awareness Training, is create “threat actor” scenarios, so here’s one:
Here is a sample OOO:
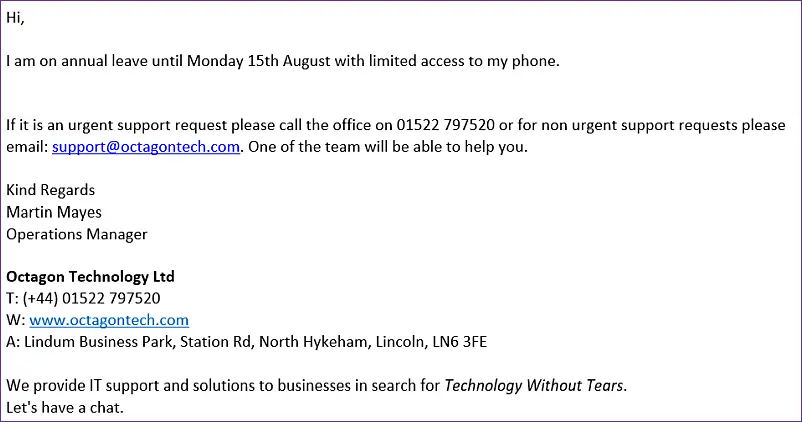
Now from this email we can see that Martin is a senior member of the team and he is out of the office until 15th August.
- Does that time range include a Friday? Social engineering attacks are more successful if carried out just before staff are heading home.
- His job is Operations Manager – which must come with some responsibility – check the company website and LinkedIn for details
- Somebody in the company will be monitoring Martin’s email and dealing with it if they can
- Are there any client details on the website – there always are, marketing tells us that testimonials bring in work!
Here is a typical phishing email that could exploit this situation.
Hi Martin
Following your instructions from last week, I still could not get access to the SharePoint folder. The proposal I was telling you about is due on Monday before 8am, can you do something to help me.
I have included the login link you sent me:
Thanks
Add a convincing signature
p.s. I will owe you a beer when you get back!
A few notes about this phishing email
- Clicking on this link would take someone to a spoofed MS365 login page that would steal the administrator credentials. Then it is 15 minutes until the compromise!
- How did they get the signature? The threat actor gets that by simply emailing one of the clients who have given a testimonial and copying it from their reply!
- Did you like the personal touch of a promise of a beer?
I now see this could be an issue. What can I do about it?
That is easy.
Have policies, procedures and training in place so when your people are on leave, their positions cannot be compromised.
When I ran this scenario past our support team, they quickly pointed out cut-outs in their systems that would have stopped this scam. Of course, I am not going to list them here and actually we keep most of them secret from the clients as well, as that is better for their cyber security.
One more thing my support team told me was that in Microsoft 365 for Business the administrator can edit the OOO’s if the user makes an error.
A couple of other ideas to make life harder for the threat actors
- Limit the information that is included in the OOO – giving the threat actors less to work with.
- Have a policy for when people are on leave – for them, their department and the business. This is essential for your most senior people and those that deal with your money, bank accounts etc.
- Consider disabling risky account authorisations for the duration of the leave period.
- Think about cut-out steps in processes – these should not depend on email
- Run a phishing simulation exercise – to give your people an experience of being hacked, with no risk.
- Sign-up for the CyberAwake training – I know it is a bit obvious, but I had to say it!
Have a happy holiday…
I do not use the OOO, a trusted member of staff shadows my email, although there are other ways of checking on my activity. There always are. We do not have a “Meet the Team”, page on the website complete with helpful photographs – I argued that one down with Marketing, but you may not be so lucky. However, I have no real control over what our people put on LinkedIn – although we have training meetings where we discuss this and what they put on social media. It helps.
One other thing. Just like many of you reading this, I check my email whilst I am away, making this type of approach less likely to work, although I can think of a couple of ways of getting around that. But that is a story for another day.
Have a good holiday. I will.
Clive Catton MSc (Cyber Security) – by-line and other articles
References
Lawson, P., Zielinska, O., Pearson, C., & Mayhorn, C. B. (2017). Interaction of personality and persuasion tactics in email phishing attacks. In Proceedings of the Human Factors and Ergonomics Society Annual Meeting (Vol. 61, No. 1, pp. 1331-1333). Sage CA: Los Angeles, CA: SAGE Publications.
Further Reading



