A few months ago, I wrote a Back-to-Basics mini-series on phishing emails, how they impact organisations and what you can do to reduce the risks.
Back-to-Basics – A Phishing Email Primer | Smart Thinking Solutions
Phish Attacks – the deluge never stops
Every week I read articles on the latest way that the threat actors have come up with to craft a phishing email and malicious package that evades the technical defences and deceives the user into clicking on the link or opening the attachment.
An article caught my eye this week on Sans Internet Storm Diary (Kopriva, 2024), that illustrated several points that I want to bring into my phishing email primer.
Old phishing email tricks still work
I am not going to get too deep into the technicalities of the attack described in the article, but the basic idea is that what at casual glance by a non-techie looks like a legitimate URL, is corrupted after the “@” sign included in that URL. This part of a URL is called the “user information string” and is useful for including legitimate user information in a URL. You can see the corrupted URL in this image from Jan Kopriva’s article:
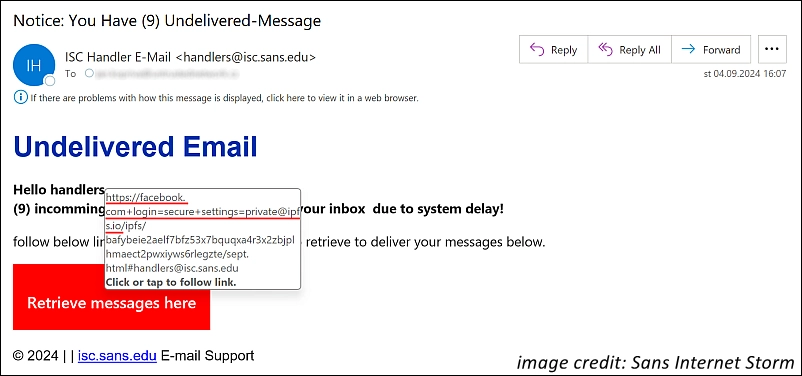
This technique and similar ones that extend malicious URLs have been used forever by attackers, and more than a casual glance is needed to decide if they are safe.
But how many phishing attacks are there?
This is a good question for the non-techie sitting at their desk, looking at their emails. I did list a few in my phishing
email primer – Phishing Primer – Phishing Types (pt. 4). That was not a complete list of phishing attacks and that brings me onto the second reason Jan’s article grabbed my attention.
It is not possible in a one or two hour cyber security awareness seminar to explain all the types of phishing emails doing the rounds and it is impossible to describe attack vectors of the future. So do not try. Your cyber security awareness training should be equipping the non-technical user with a range of tools that allows them to spot suspicious communications. They need to know how to react to their suspicions and if the worse happens, what to do.
Our Cyber Security Awareness Training does just that.
Next
I will get back to our mini-series on Bring-Your-Own-Device. You can catch part one of that series here: BYOD Bring-Your-Own-Device – A Primer (pt.1)
Clive Catton MSc (Cyber Security) – by-line and other articles
References
Kopriva, J. (2024). Phishing links with @ sign and the need for effective security awareness building. SANS Internet Storm Center. https://isc.sans.edu/diary/Phishing%20links%20with%20@%20sign%20and%20the%20need%20for%20effective%20security%20awareness%20building/31288


