The scammers – sorry, cyber criminals – who masquerade as the delivery firm Evri, have been up to their old social engineering tricks again!
A couple of weeks back, whilst waiting for a delivery by Evri, I received a scam text message and I wrote about that experience here:
Social Engineering
The classic “putting you under pressure” approach is being used here again – you want your parcel, then do this – and if you are in a hurry or the package is important, you may fall for it and carry out the criminals’ wishes.
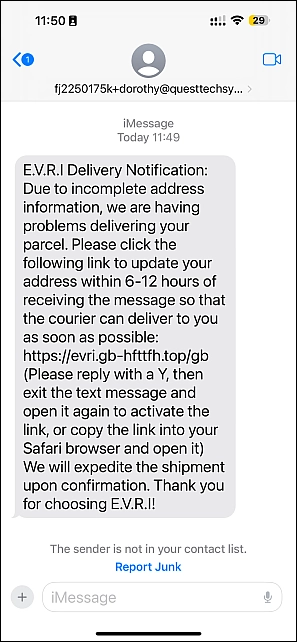
Of course, you have to be waiting for a package to be delivered for this to work, and of course, this time I was not expecting anything, so there was no risk of me being scammed – unlike last time when I was waiting and I had my music playing too loud!
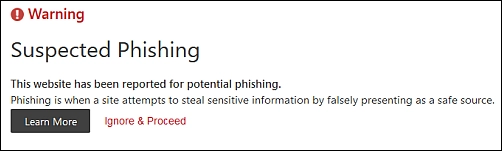
I did not follow the link this time – I am going to assume it would have taken me to the same information-stealing webpage as the last attack.
Something different this time
Unlike last time, the scammer was not using a gmail.com account, but there was a domain I could recognise.

With a domain, I can have a deeper dive into who is what?
First, I simply put the domain into my browser – but no joy:
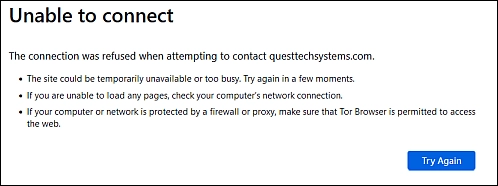
I was not really expecting a scammer’s home page to appear. Then I put the domain into whois to have a look at what details were available there.
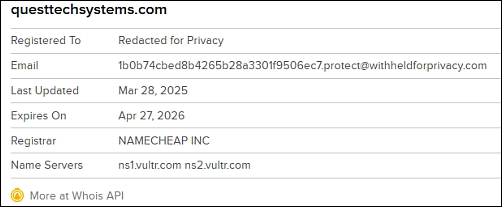
So, for their own privacy, the contact email address and the registration are withheld for privacy – it is good to know that these scammers have a sense of humour. I’ll come back to whois in a moment.
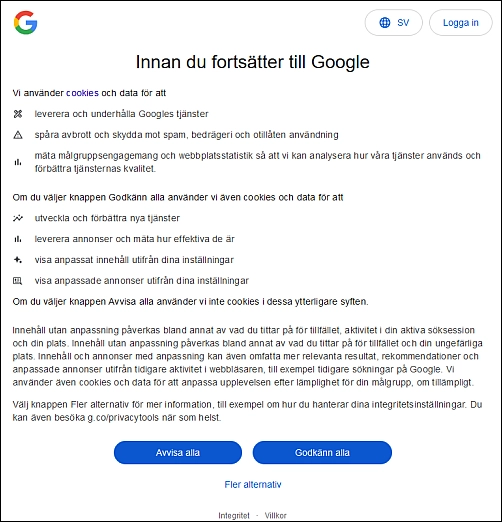
The last thing I tried was putting the rogue URL into my Linux browser to see what would happen if I did not activate the link first, and that, after a suitable delay, redirected me to the Swedish version of Google.
Back to whois?
There was one useful bit of information from Whois – the registrant NAMECHEAP INC – we have an account with them, so I logged in and reported this domain as malicious.
Social Engineering – Your Takeaway
There are two.
1 Do not do what I did. Following malicious links and opening malicious websites is not something you want to do on either your personal or work computers or devices. I carried this project out on my isolated Linux laptop using a separate VPN-protected internet connection and several other cutouts and security steps. I was warned!
2 Social engineering is an effective tool for cyber criminals – training your team in what to expect from phishing and social engineering attacks is an essential element in any organisation’s cyber security plans. Have you looked at our Cyber Security Awareness Training?
Cyber Security Awareness Training – Why? | Smart Thinking Solutions
Clive Catton MSc (Cyber Security) – by-line and other articles
Further Reading
On the real Evri domain, there is helpful information on how to recognise real Evri communications:
Is this Evri Text/Email Genuine? | FAQs | Evri
Photo by cottonbro studio


