I am a big user of OneNote. I find it a great tool for connecting my Apple devices to my Microsoft world, for always having that note from a meeting 12 months ago to hand and to find that place of interest I saw on TV whilst on holiday, etc., etc., etc.. Because I love it, my companies love it(well they have to!) and we use it a lot to enable projects and share information – again across various platforms and device.
If we find it useful then others must find it as useful – Apple has even recently launched it’s own OneNote clone called FreeForm. So I should not be surprised that threat actors have found a vulnerability in it that they can exploit:
Hackers now use Microsoft OneNote attachments to spread malware (bleepingcomputer.com)
The attachment extension is “.one”.
It is an old style of attack, a phishing email, with a plausible story to catch you into opening the OneNote file. From there the world of malware opens up for the threat actors, from stealing credentials to encrypting files.
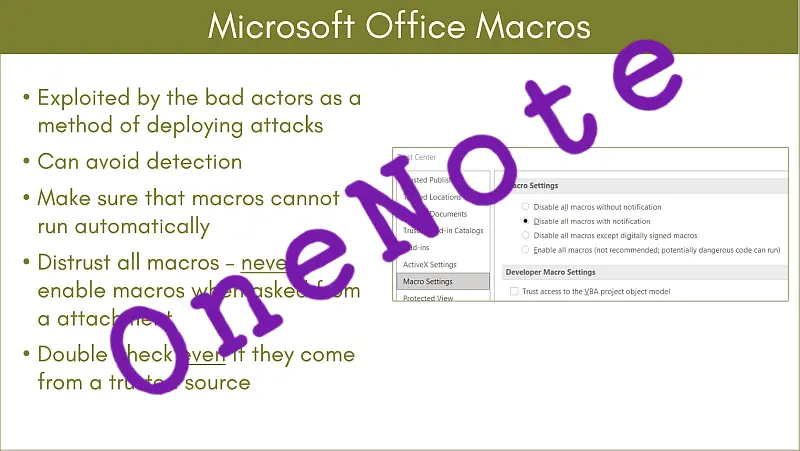
Macros Disabled
The only good thing from this sorry story is that following Microsoft’s ping-pong attempts to close the macro vulnerability in Office tools, which resulted eventually in macros being disabled by default – so making this an unreliable attack vector.

However…
We have clients who have had us re-enable macros on their machines, because they are using the great functionality that macros offer to them, as part of their daily work. These people tend to be accountants and managers, using the various modelling capabilities in Excel, although we do have clients using macros to automate some of the repetitive tasks in Word across the whole of their team. So the “send an Office file with an embedded malicious macro” attack vector still exists and it is probably being used by senior people in an organisation who would be a great target for threat actors.
From experience there is one more interesting thing about this group of senior managers, they are most likely to be ones who are to busy, or just happen to have another meeting scheduled when t comes to attending the staff cyber awareness training. (Just the other week when I was discussing this very matter with a CEO, we discovered from the training reports we generate from our online training platform that nearly half of her senior team still had not completed the training.)
Your takeaway from this…
You should only give macro access to those members of your team who really use it (not just think they need it) and you should make sure everyone is cyber aware for when the technical cyber security defences are not enough.
Clive Catton MSc (Cyber Security) – by-line and other articles
p.s.
This type of attack is not directly aimed at compromising OneNote itself, so if you are storing your passwords in an encrypted OneNote notebook, they are still secure.
Further Reading
A First Malicious OneNote Document – SANS
Our online training