I am reposting this article as I spent too much time yesterday, whilst on leave, convincing a business owner that they needed to implement Microsoft 365 multi-factor authentication for everyone. Passwords are not enough. Original Post Eventually yes: Something better than a password – Passwordless Authentication – CyberAwake
ESXiArgs Ransomware Recovery Advice
Following the discovery of a coding flaw in the ESXiArgs Ransomware, the US government Cybersecurity and Infrastructure Security Agency (CISA) and the FBI have released a document outlining how to use the various scripts and processes to recovery data after an attack: CISA and FBI Release ESXiArgs Ransomware Recovery Guidance …
Minimise the Damage – Planning and Preparation – Ransomware Part 3*
I have a companion article to this one to this one looking at the planning and preparation needed if you are not plugged in! Pull the Plug: But I haven’t got a plug! In my previous ransomware article, in this mini-series, we had a quick look at some spanners and …
Continue reading “Minimise the Damage – Planning and Preparation – Ransomware Part 3*”
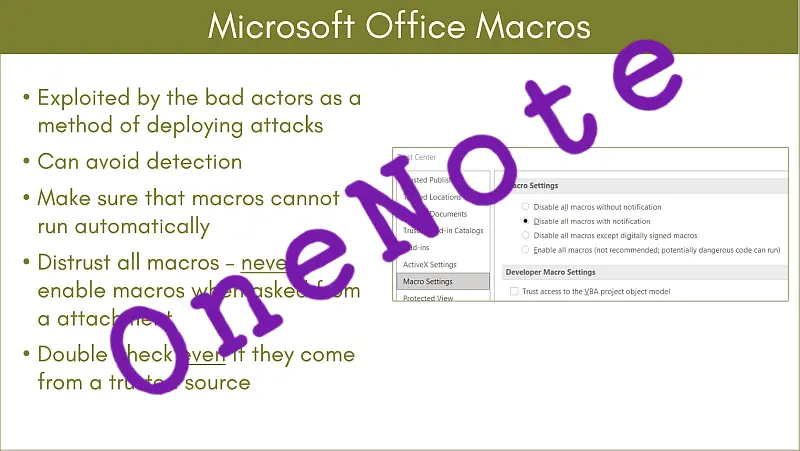
QakNote – OneNote malware now has name
I use OneNote a lot – so I had to follow up on my previous post about OneNote attachments being used as an attack vector. OneNote has become the threat actors new choice of attachment probably because Microsoft closed the door on macro attacks. In the wild, Microsoft OneNote’ .one’ …
Ransomware Advice – The Bite Sized Mini-series
My ongoing ransomware advice mini-series, continued yesterday with part 2 being published on CyberAwake: A Bag of Spanners – Planning and Preparation I am publishing the series across all three of the blogs I regularly write for, Smart Thinking, Octagon Technology and CyberAwake – part 1 is available at Octagon …
Continue reading “Ransomware Advice – The Bite Sized Mini-series”