We have published another part of our series on the cyber security risk every organisation faces and what you need to do about it. I say we, as Diana and I are writing it together. The Risks So Far Risk. Where do you start? Risk Appetite Risk Assessment – Understanding …
China and US Outlook Online cyber attacks
Microsoft has reported to the US government that it has monitored Chinese threat actors gaining access to the email of various organisations including US government departments. Microsoft: China accused of hacking US government emails – BBC News Microsoft alleges China behind attack on Exchange Online • The Register China denied …
Continue reading “China and US Outlook Online cyber attacks”
Risk
Recently, I have been talking a lot with clients about risk. Some clients can see the point and are moving with us to work on those risks, others are harder to convince. I have an article on CyberAwake looking at the start of a risk journey: Risk. Where do you …
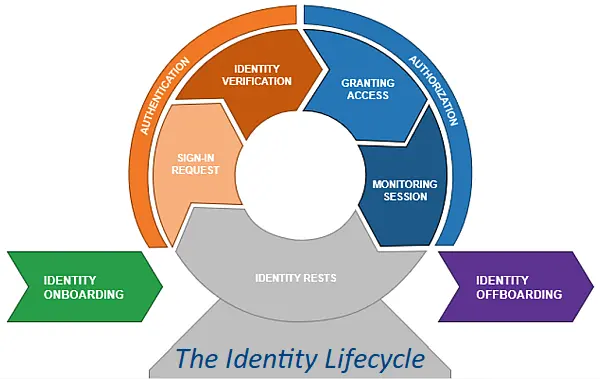
Authentication – Who Do You Let In?
Authentication, Authorisation and Accountability. This is the first part of a three-part series looking at the basics of the cyber security principle of “AAA”. Today we will start with Authentication It seems the easiest of principles. Everyone needs a username and password (credentials) to access any of your organisation’s systems. …
Risk Analysis – How to eat a very large quadruped!
Today we are going to look at the very first meeting I have with clients where we look at risk analysis. This is not a blog about eating an elephant – that is a figure of speech – although I do have a book that includes a paragraph or two …
Continue reading “Risk Analysis – How to eat a very large quadruped!”