An air-gapped system is designed to be very secure. It is not connected to any other system, network or internet – literally a physical gap between it and the rest of the IT world. If it is not connected, then threat actors cannot connect to it. Mordechai Guri, from Ben-Gurion …
Is there censorship on the web?
Of course there is, and in some surprising places. Here is a report by the The Citizen Lab, examining how Microsoft Bing censors autosuggestions on politically sensitive Chinese names and other topics. This is not only applied in China, as we would expect, but in other regions too! Bada Bing, …
Cyber criminals start an actual fire at a plant
A cyber gang, Predatory Sparrow, have claimed to have taken control of plant at a steel works in Iran and caused it to malfunction. There is CCTV footage showing the machinery malfunctioning and plant workers fleeing the area. Predatory Sparrow: Who are the hackers who say they started a fire …
Continue reading “Cyber criminals start an actual fire at a plant”
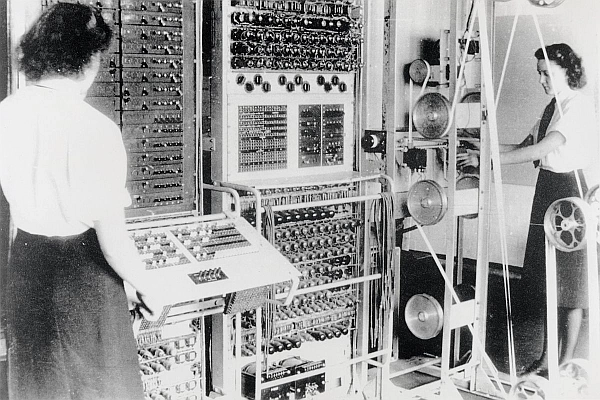
What is a cryptopocalypse?
We have come a long way in cryptography and computing since the Colossus electronic computer, (above), was built at Bletchley Park, during the Second World War, to break the Lorenz cipher. With the advances in computing technology, there is a foreseeable point in the future, possibly only ten years, when …
This is a technology exercise in when everything goes wrong!
I was put onto this blog post via Bruce Schneier’s blog. I’ve locked myself out of my digital life – Terence Eden’s Blog (shkspr.mobi) This is why role play and thinking about your operation, is a vital part of creating a cyber security plan that is resilient and provides for …
Continue reading “This is a technology exercise in when everything goes wrong!”