What exactly do I mean when I say “ransomware resilient back-up”?
I was going to write about redacting today, but I got a call from a cyber security client who needed some information for their insurance company about the back-ups we supply them and then she asked the question “what is a ransomware resilient back-up?”. Here is the answer.
The National Cyber Security Centre and Back-up
As part of the UK’s national security infrastructure, The National Cyber Security Centre deals with some of the biggest cyber security issues facing the country, but they recognise that it is the small things that build a secure cyber security framework and so are charged with producing advice for everyone. In their advice about back-ups the first thing they want people to be aware of is that a back-up that will help you recover from an encryption ransomware attack has to be disconnected from your system, so it cannot be attacked or encrypted. (NCSC, 2022)
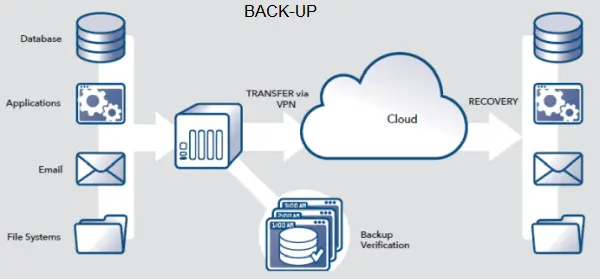
Now you need to compare all your back-ups with this list to see whether they are good enough for the job.
My ransomware resilient back-up list
- Automatic – no one should have to swap drives or worse still tapes (it is at this point that every IT professional is reliving nightmares of verified tape back-ups that did not work in a crisis)
- Scheduled – the back-up has to be regular to be effective
- Fast recovery – when you need your back-up you are usually in a hurry.
- Offsite – to a site that is secure and located in the UK
- Disconnected from the original data – this is one of the most important parts of the ransomware resilience. If the back-up is not connected to an infected network then it cannot be encrypted.
- Encrypted at the storage location – this means that threat actors cannot read your information in the data centre and that authorised recovery will need a decryption key
- Transmitted offsite securely – this is important, unencrypted USB sticks in someone’s pocket do not meet the standard.
- Have an effective retention for both cyber security and business operations. Retention is a fancy name for keeping a series of previous days’ copies of the back-up data. This allows you to:
- Go back before the encryption attack and start recovering unencrypted data
- When it comes to operations it is useful when one of the team accidentally deletes a folder or file and discovers the issue weeks later
- Managed and checked daily – obvious really and no excuses
- Tested – so you know that it will work when you need it
- There is a problem…
The Double-Extortion Variant
Ransomware was very lucrative for the threat actors when it first started circulating and most back-ups were not up to the task of giving an effective escape route. But as the threat and risks increased, users started to get better and better back-ups and the illicit profits dropped.
It did not take long for the well organised ransomware gang to realise that once they had compromised a system for encryption they could exfiltrate a copy of the data offsite at the same time. Now they had a double extortion over the victim:
- Pay up for the decryption key – but if you have a back-up escape route you don’t have to pay
- Pay up or we release your sensitive and private data to the Dark Web for other threat actors to see if they can find a vulnerability to exploit or to the public domain to embarrass and impact your operations.
Now you can see why a ransomware resilient back-up is not the whole story.
Later…
Having got to this point of explaining what I feel the minimum requirements for a back-up are, I realise that I will be coming back to this subject in the future and looking at how the “principle of least privilege” can help when it comes to threat actors’ data exfiltration.
Clive Catton MSc (Cyber Security) – by-line and other articles
References
NCSC. (2022). Offline backups in an online world. NCSC. Retrieved November 30, 2022, from https://www.ncsc.gov.uk/blog-post/offline-backups-in-an-online-world

