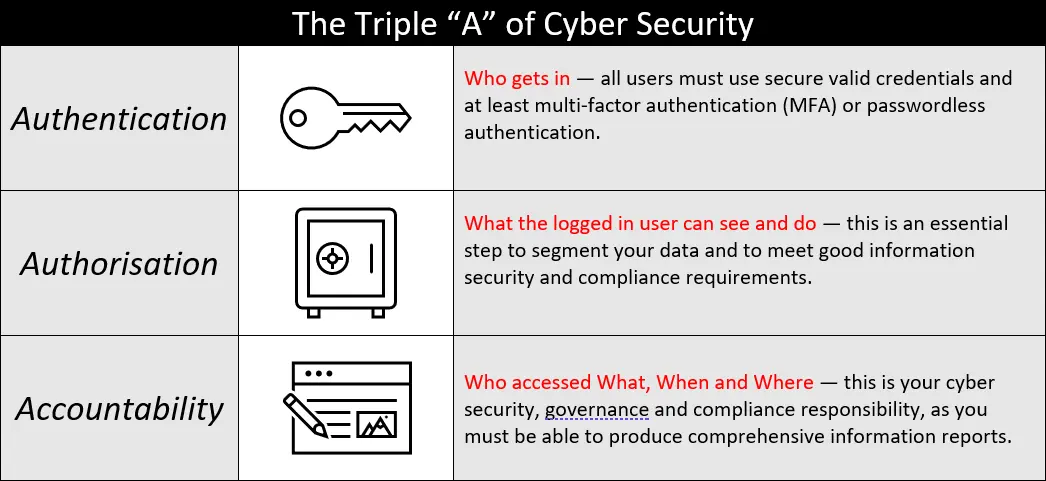
AAA = Authentication, Authorisation and Accountability AAA is a vital step in any cyber security strategy is: AAA, the first two As gives you the ability to control who has access to your information and what information they are able to see. The third A is accountability – without this …
Identity
I have been covering identity, credentials and authentication in our Summer webinar series – if you have not registered to attand it is not too late, as registration will also give you access to the recordings of the webinars you have missed. Digital identity and proving who you are is …
WhatsApp security concerns
This ban is about cyber security concerns with using WhatsApp to conduct official US government business in the U.S. House of Representatives The House’s Chief Administrative Officer (CAO) has classified WhatsApp “as a “high-risk” communication platform” and suggests staff pick an alternative app such as Microsoft Teams or Signal. US …
Hack Me If You Can – Think You’re Unhackable? Think Again.
We’ve all heard it: “It won’t happen to me.” Usually said moments before it does happen to you – whether it’s locking your keys in the car, burning the toast, or falling victim to a phishing email from “Your CEO” asking for iTunes vouchers. Let’s face it – in today’s …
Continue reading “Hack Me If You Can – Think You’re Unhackable? Think Again. “
Hack Me If You Can! What’s your excuse?
“I am too busy for cyber security.” “It will never happen to me.” “My organisation is too small for the hackers to bother with.” “HMRC hacked for £42M because someone’s login was compromised.” FAKE NEWS!!!! “Cyber security is hard – when I remember, I will get someone else to fix …