As part of the Cyber Security Awareness Training I deliver, I always emphasise that any credentials people are entrusted with have a value and should be protected accordingly. Here is the proof of that statement – credentials for sale: ‘Russian Market’ emerges as a go-to shop for stolen credentials – …
Signal for privacy
The secure messaging app Signal has made the news recently with various members of the US Government using it to avoid accountability (possibly) and to inappropriately share their thoughts on secret operations with journalists and then the rest of the world (accually). I am a Signal user – I like …
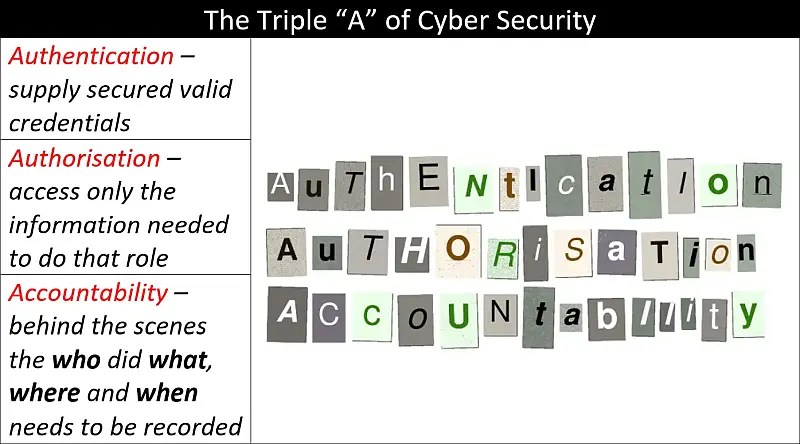
Authentication, Authorisation and Accountability – A Primer
Authentication, Authorisation and Accountability (AAA) and The Principle of Least Privilege (PoLP) come together in this primer to give you a basic understanding of the importance of knowing who is accessing your information and how much they can access. Another important idea covered here is what happens when something goes …
Continue reading “Authentication, Authorisation and Accountability – A Primer”
Signal app in the news.
I use, and recommend to clients, the secure messaging app Signal, for those communications that do not require accountability but do require good cyber security. However, it is not an app suitable for government communications that usually require a higher level of security and should always include accountability to the …
Signalgate
I am not sure anyone is actually calling it that… We have all seen and or heard of this story that is running in the US and around the world: Trump and intelligence chiefs play down Signal group chat leak – BBC News I am not going to get into …