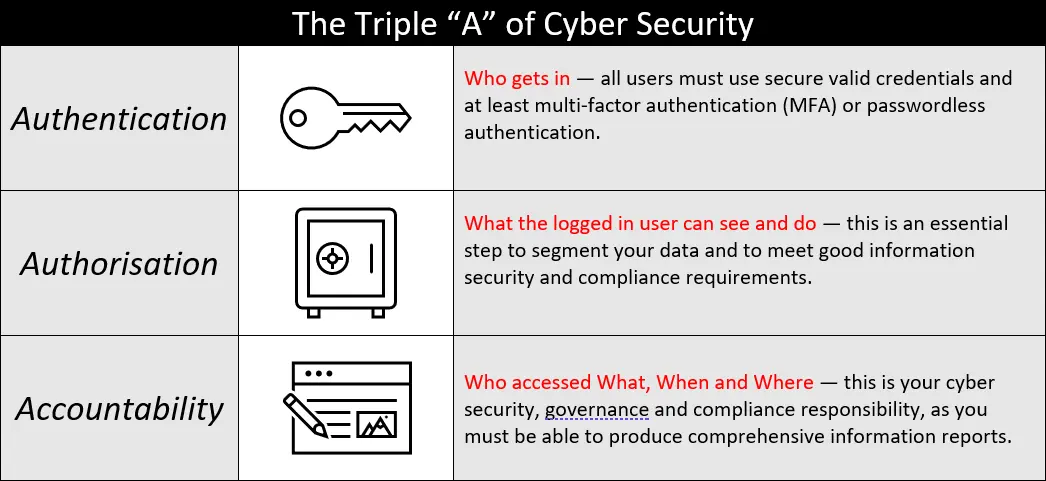
AAA = Authentication, Authorisation and Accountability AAA is a vital step in any cyber security strategy is: AAA, the first two As gives you the ability to control who has access to your information and what information they are able to see. The third A is accountability – without this …
Back to Basics – Why MFA? (pt.3)
In this third part of my MFA mini-series, I am going to look at some of the resistance that we get when trying to implement multi-factor authentication. MFA – It is like medicine that tastes bad In the first part of this series, I briefly explained the highlights of why …
What’s Wrong with MFA
This is the second part of my Back-to-Basics MFA mini-series. Having spent last week’s article telling you how great Multi-factor Authentication is and how you and everyone in your organisation needs to use it for every service that offers it, today we are going to look at one of the …
Back to Basics – MFA
Use MFA or Multi-factor Authentication. End of article, well not quite… So you have heard of MFA but let’s clarify why it is a good idea I am not going to go into the technicalities of how MFA works – I have included a link below if you want to …
Identity
I have been covering identity, credentials and authentication in our Summer webinar series – if you have not registered to attand it is not too late, as registration will also give you access to the recordings of the webinars you have missed. Digital identity and proving who you are is …