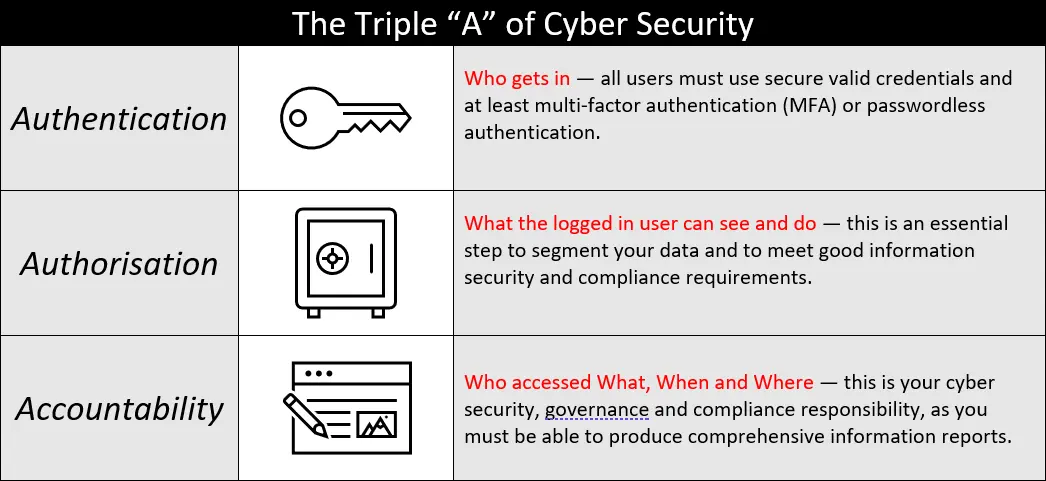
AAA = Authentication, Authorisation and Accountability AAA is a vital step in any cyber security strategy is: AAA, the first two As gives you the ability to control who has access to your information and what information they are able to see. The third A is accountability – without this …
Hack Me If You Can – Think You’re Unhackable? Think Again.
We’ve all heard it: “It won’t happen to me.” Usually said moments before it does happen to you – whether it’s locking your keys in the car, burning the toast, or falling victim to a phishing email from “Your CEO” asking for iTunes vouchers. Let’s face it – in today’s …
Continue reading “Hack Me If You Can – Think You’re Unhackable? Think Again. “
Hack Me If You Can! What’s your excuse?
“I am too busy for cyber security.” “It will never happen to me.” “My organisation is too small for the hackers to bother with.” “HMRC hacked for £42M because someone’s login was compromised.” FAKE NEWS!!!! “Cyber security is hard – when I remember, I will get someone else to fix …
Credentials Matter
As part of the Cyber Security Awareness Training I deliver, I always emphasise that any credentials people are entrusted with have a value and should be protected accordingly. Here is the proof of that statement – credentials for sale: ‘Russian Market’ emerges as a go-to shop for stolen credentials – …
Authentication, Authorisation and Accountability – A Primer
Authentication, Authorisation and Accountability (AAA) and The Principle of Least Privilege (PoLP) come together in this primer to give you a basic understanding of the importance of knowing who is accessing your information and how much they can access. Another important idea covered here is what happens when something goes …
Continue reading “Authentication, Authorisation and Accountability – A Primer”