This week the Wednesday Bit is for reminding you about my collection of mini-series and back to basics cyber security primers. There have been a number of additions, updates and changes since I first ran a “Collection” article. Why am I doing this? Because we can all benefit from some …
The Principle of Least Privilege and Authentication, Authorisation and Accountability – A Primer
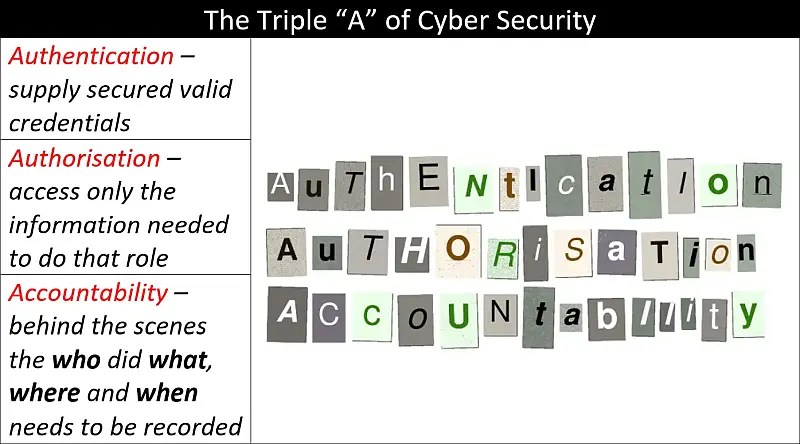
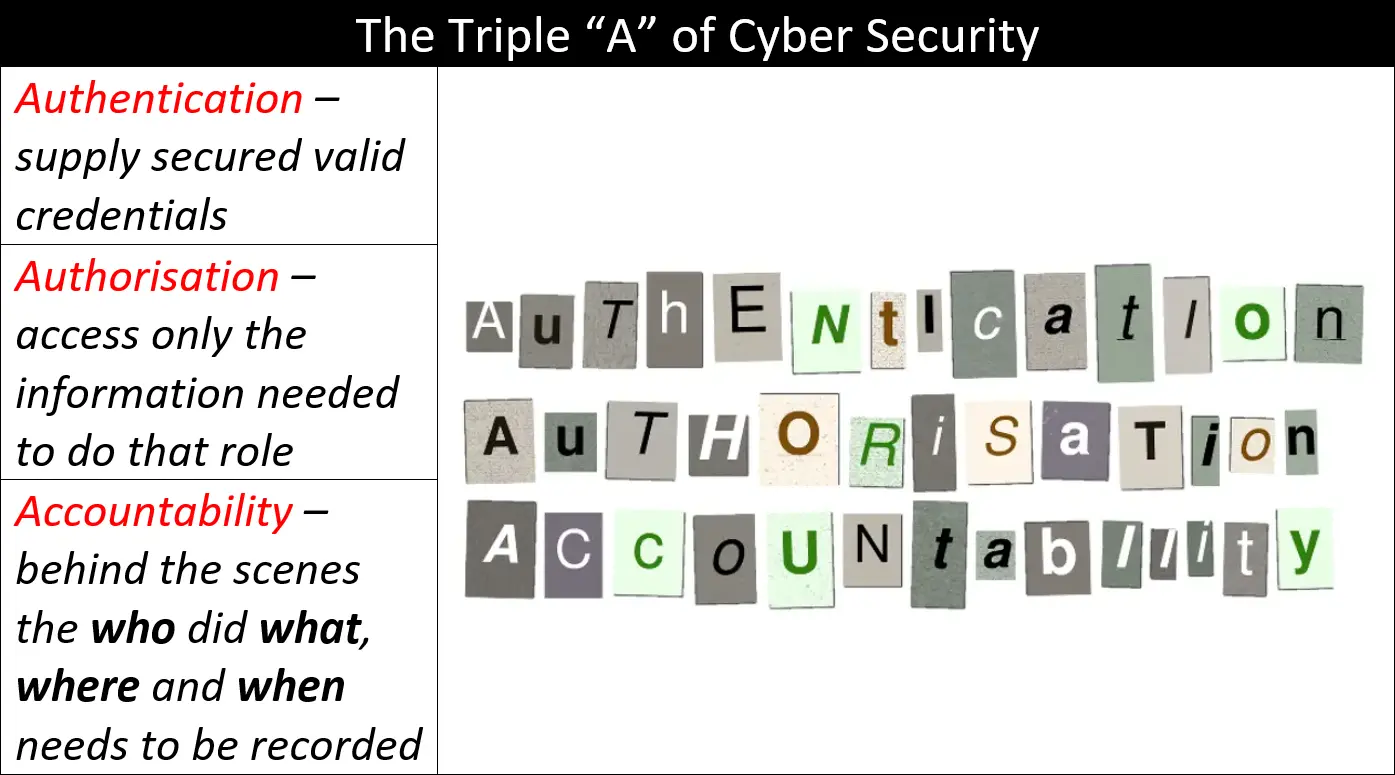
Authentication, Authorisation and Accountability (AAA) and The Principle of Least Privilege (PoLP) come together in this primer to give you a basic understanding of the importance of knowing who is accessing your information and how much they can access. Another important idea covered here is what happens when something goes …
What the “Principle of Least Privilege” does for you? (pt. 1)
This article follows on from last week’s Why the “Principle of Least Privilege” works and something for free…. If you want the something for free, then you had better read that article first! Let’s start with a simple definition. The Principle of Least Privilege (PoLP) is a fundamental concept in …
Continue reading “What the “Principle of Least Privilege” does for you? (pt. 1)”
Back to Basics – The Collection.
This week the Wednesday Bit is about is highlighting some of the mini-series and back to basics cyber security primers I have written. Why? Because yesterday when I was speaking with a long-term client about password hygiene in their organisation, they were unaware I had a Password Primer they could …
“View Document”
Sometimes a cyber-attack is something as easy as adding a button saying “view document” when whale phishing senior people in an organisation. Ongoing Microsoft Azure account hijacking campaign targets executives (bleepingcomputer.com) Your takeaway When was the last time you audited the credentials and associated authorisations of those credentials? If you …
Talk! Talk! Cyber Security Awareness
For those of you who read Smart Thinking regularly, you will realise that this “Wednesday Bit” has been published a day late – the reason was a Cyber Security Awareness talk I gave yesterday at the East Lincs Expo. I delayed publishing, rather than writing an article and leaving it …
Insider Threat – How would you feel if someone betrayed your trust?
What is the Insider Threat? The insider threat is one of the most difficult cyber security issues to deal with as it involves someone you trust betraying that trust behind your back. They betray that trust and exploit the access they have to privileged information or processes. Unfortunately the insider …
Continue reading “Insider Threat – How would you feel if someone betrayed your trust?”