I use AirDrop occasionally, to be honest it is usually between family and friends, but I have been known to use it at events and conferences to swap contact details with other attendees – it is very convenient. Now research is emerging from China that this convenient Apple tool may …
X – The Wild West of the Internet
It looks like Elon Musk’s social network X has become the new favourite place for threat actors who want to distribute their malware, especially malicious crypto-malware. X users fed up with constant stream of malicious crypto ads (bleepingcomputer.com) Hackers hijack govt and business accounts on X for crypto scams (bleepingcomputer.com) …
Where to start in 2024?
Happy New Year. I am going to start the cyber news for 2024 with a story that broke between Christmas and the New Year – Apple iPhone hardware vulnerabilities. I am a great supporter of the Apple iPhone and the associated “walled garden” App store as a good cyber security …
Chrome gets updates
Google is always on the lookout for security issues Google Chrome and Chromium – many other browsers are based on this technology including Microsoft Edge so it is a rich target for threat actors if they can find a flaw to exploit. When those patches are issued you or your …
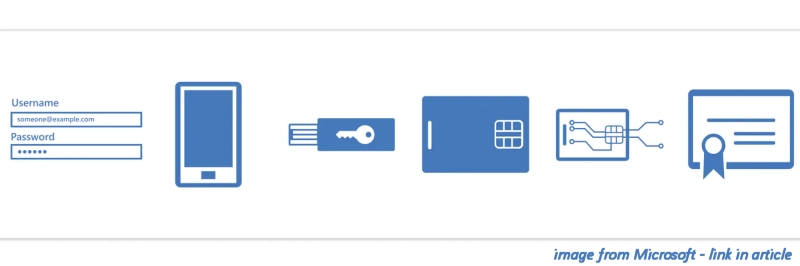
Unsolicited MFA prompts
Last Wednesday I published my MFA Primer series and part two looks at this type of cyber attack against multi-factor authentication. In brief when the threat actors have a valid set of credentials they repeatedly try and access the service with them, generating multiple MFA requests to your authenticator app. …