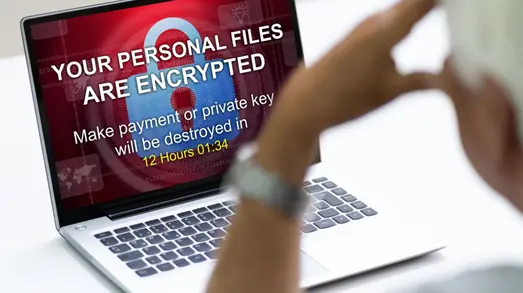
It is not possible to forget ransomware, just this week our engineers have updated a client’s back-up to one that is ransomware compliant – meaning, among other things, that the threat actors cannot access and so encrypt or alter the back-up during their attacks. Up to this point the client …
Continue reading “Just when you thought I had forgotten about ransomware”