Bruce Schneier’s blog put me onto this article, which explains in some depth how with careful detective work, and open-source intelligence (OSINT) made anonymous cryptocurrency transactions not so anonymous. It is a long, but very interesting article but please note the content warning from the Wired website, and do not …
Ukrainian power grid hack thwarted
This story is doing the rounds everywhere. A joint effort between ESET and Ukraine Computer Emergency Response Team (Cert-UA) defeated the attack, discovering a new variant of the Industroyer malware – which was used in a previous attack on the Ukrainian power grid in December 2016. This malware is associated …
Even the world’s biggest companies get suckered by social engineering
Both Apple and Meta were the victims of social engineering scams that caused them to simply giveaway user personal information. I am not going to call this sophisticated – actually it was quite simple – the cyber criminals, studied how an Emergency Data Requests (EDR) operated and then spoofed that …
Continue reading “Even the world’s biggest companies get suckered by social engineering”
Google block’s a North Korean Chrome exploit -UPDATED
This story was first posted on 25 March 2022 This story This attack used classic social engineering tactics – the hackers posed as recruiters for a dream job or set up a bogus websites aimed at financial and crypto-currency industries – to exploit a remote code vulnerability in Google Chrome. …
Continue reading “Google block’s a North Korean Chrome exploit -UPDATED”
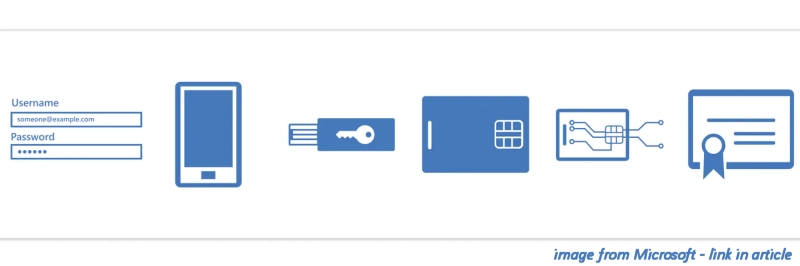
MFA is essential but it has it’s issues
We are always insisting that our clients always use multi-factor authentication (MFA) for absolutely every service they use. It is a prerequisite of any client we manage Microsoft 365 for that MFA is activated and enforced for everyone of their users. However, of course, there are ways that hackers exploit …