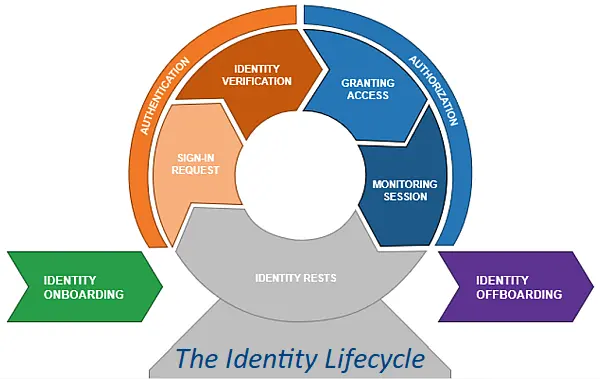
Authentication, Authorisation and Accountability. This is the first part of a three-part series looking at the basics of the cyber security principle of “AAA”. Today we will start with Authentication It seems the easiest of principles. Everyone needs a username and password (credentials) to access any of your organisation’s systems. …
Biometrics
I had this article published yesterday on CyberAwake looking at biometrics and cyber security: We all thought biometrics were better security… (cyberawake.co.uk)
If you use KeePass it is good to know…
…it does not leak your master password any more! I have had a lot to say on the storage of your highly sensitive passwords – use an online bank if you must but also realise they are not perfect: KeePass v2.54 fixes bug that leaked cleartext master password (bleepingcomputer.com) I …
The Capita hack keep gathering victims
Capita is the largest outsourcing company in the UK and counts among it’s contracts the UK Government, the Ministry of Defence, local authorities and businesses. When Capita’s security was breached it was going to lead to an ever increasing list of victims as the investigation proceeded. Capita hack: 90 organisations …
PyPi software repository takes the most basic of security steps…
Having temporarily closed its doors last week to new business, PyPi – a python code repository – is now enforcing the most basic of cyber security precautions – 2FA! PyPI announces mandatory use of 2FA for all software publishers (bleepingcomputer.com) Your takeaway from this is that any essential business service …
Continue reading “PyPi software repository takes the most basic of security steps…”