I am not sure anyone is actually calling it that… We have all seen and or heard of this story that is running in the US and around the world: Trump and intelligence chiefs play down Signal group chat leak – BBC News I am not going to get into …
Booking.com phishing attacks
We use Booking.com for our business travel, so this story was going to make the news this week. ClickFix attack delivers infostealers, RATs in fake Booking.com emails This is a long running phishing campaign that is obviously still having success in trapping victims – targeting organisations that use Booking.com for …
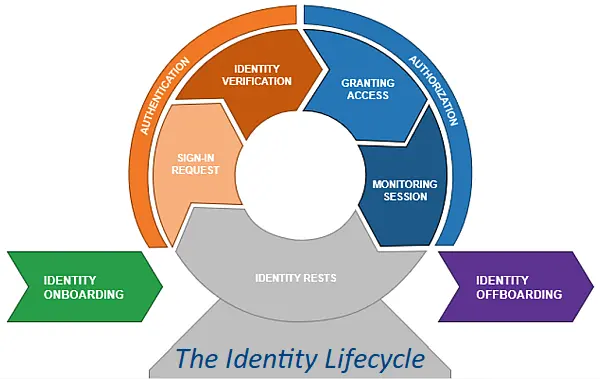
Identity Theft (part 1)
Identity theft, as cyber attacks go, is pretty easy to understand – a threat actor gains control of a user’s credentials (identity) and then attacks the service (organisation), posing as that user. There are nuances but that is the attack in the briefest of terms. Credential and identity theft are …
Attacks on M365 Credentials
It still works, set up a lot of devices to just try their luck to break into as many M365 accounts as possible – it will work sometimes. In this case over 100,000 devices have been hijacked to create a botnet that also side steps MFA security using an outdated …
Threat Actors want your Microsoft 365 Credentials
Many of my cyber security investigations have involve the compromise of Microsoft 365 credentials. These are a valuable commodity for threat actors, as a carelessly managed set of credentials may give them the keys to raid your information. The latest attack on M365 credentials, in the tech news, is a …
Continue reading “Threat Actors want your Microsoft 365 Credentials”