Well the fine in the case of the massive outsourcing firm, Capita, who did not adequately protect the information of over 6.5 million victims – £14M. Capita fined £14m for cyber-attack which affected millions – BBC News Here is a recap of the Capita hack from mid-2023: The Capita Data …
Cyber-attacks
Here are two informative articles from the BBC looking at two different cyber-attacks. The first is a look at an attack on Redcar and Cleveland Council in February 2020, which for the rest of us got overtaken by world events but for those living and working in the region it …
If your plan to defeat ransomware is to pay up then read on…
With the cyber-attacks on UK retail stores making the headlines over the last couple of weeks, I thought I would rerun this article (from CyberAwake, August 2022) on the pros and cons of paying the ransomware gangs. NCSC and the ICO say – Don’t pay the malware ransom. A couple …
Continue reading “If your plan to defeat ransomware is to pay up then read on…”
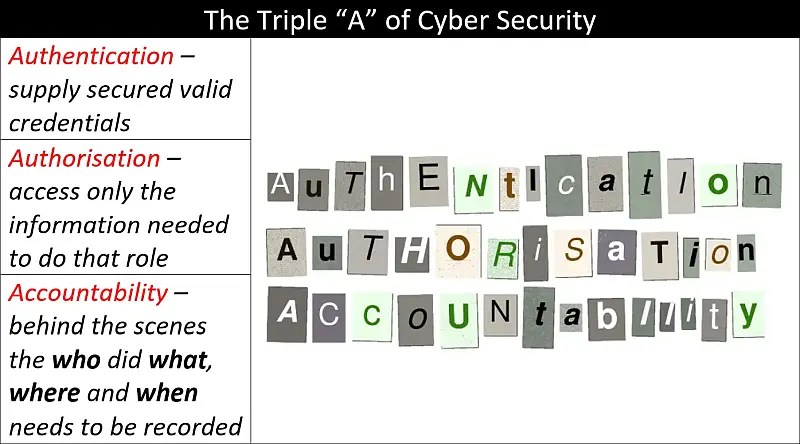
Authentication, Authorisation and Accountability – A Primer
Authentication, Authorisation and Accountability (AAA) and The Principle of Least Privilege (PoLP) come together in this primer to give you a basic understanding of the importance of knowing who is accessing your information and how much they can access. Another important idea covered here is what happens when something goes …
Continue reading “Authentication, Authorisation and Accountability – A Primer”
The Principle of Least Privilege – A Primer
Understanding the principle of least privilege – and then applying it in your organisation – is a fundamental step towards better cyber security. To help you gain the underpinning knowledge as to why this is important, I have written the following two articles: What the “Principle of Least Privilege” does …
Continue reading “The Principle of Least Privilege – A Primer”