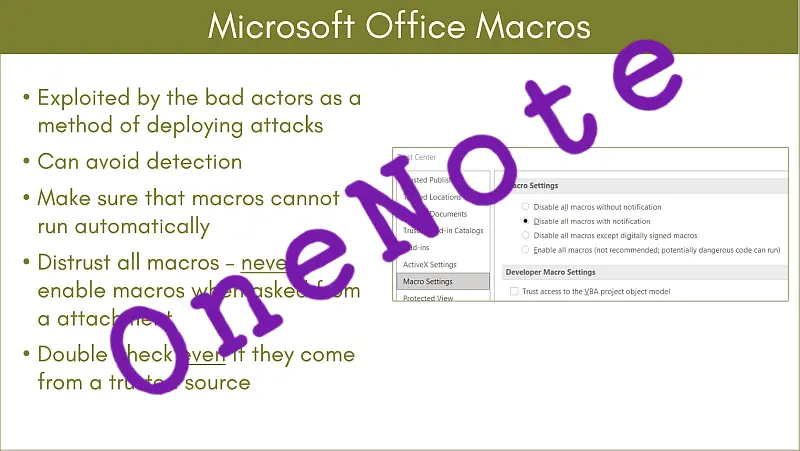
Following the recent increase in cyber attacks using Microsoft OneNote .one attachments as the carrier, OneNote is to get some enhanced security updates from Microsoft. Although it looks like we will have to wait for this extra protection from high risk phishing attacks until the end of April 2023. Microsoft …
Last week it was Eurovision this week it is a collapsed bank…
…internet scams. But for scam read theft! I am always trying to raise the awareness of any active online criminal activity associated with any human event or disaster. This week’s candidate is the collapse of Silicon Valley Bank (SVB). Since the collapse, even though I am not a SVB customer …
Continue reading “Last week it was Eurovision this week it is a collapsed bank…”
Ransomware Mini-Series
The Ransomware Mini-Series comes to an end this week, with the final part scheduled to be published tomorrow on CyberAwake. There are two articles about the impact of ransomware in the news today. One shows how more than a year after the original attack Gloucester City Council are still dealing …
IceFire ransomware encrypts both Windows and Linux systems
Now your Linux servers will be encrypted with a new variant of the IceFire ransomware.. You do not have Linux, then the malware will switch to its Windows version. IceFire ransomware now encrypts both Linux and Windows systems (bleepingcomputer.com) Ransomware will always be adapting – you need to as well. …
Continue reading “IceFire ransomware encrypts both Windows and Linux systems”
The Ransomware mini-series is almost complete
The penultimate part of my mini-series looking at Ransomware has been published today on CyberAwake: Before – Ransomware Part 9 – CyberAwake Here are the rest of the parts – published across Smart Thinking, CyberAwake and Octagon Technology. Ransomware Mini-Series (2023) Ransomware: Is it a Threat? (Part 1) A Bag …
Continue reading “The Ransomware mini-series is almost complete”