Here are a couple of stories showing that ransomware hits large and small organisations: Luxembourg energy companies struggling with alleged ransomware attack, data breach – The Record by Recorded Future At least 34 healthcare orgs affected by alleged ransomware attack on OneTouchPoint – The Record by Recorded Future The Bromford …
Seasonal article over on CyberAwake
With the holiday season well underway, I thought we would take a look at the cyber security implications of the Out-of-Office notification:
It takes only 15 minutes for the threat actors to start scanning for vulnerabilities when they are discovered.
How quickly do you respond to gaps in your cybersecurity? It is obvious but even the biggest organisations and governments in the world will be responding slower that the threat actors – so there will always be gaps in the cyber security. Hackers scan for vulnerabilities within 15 minutes of …
New ransomware article on CyberAwake
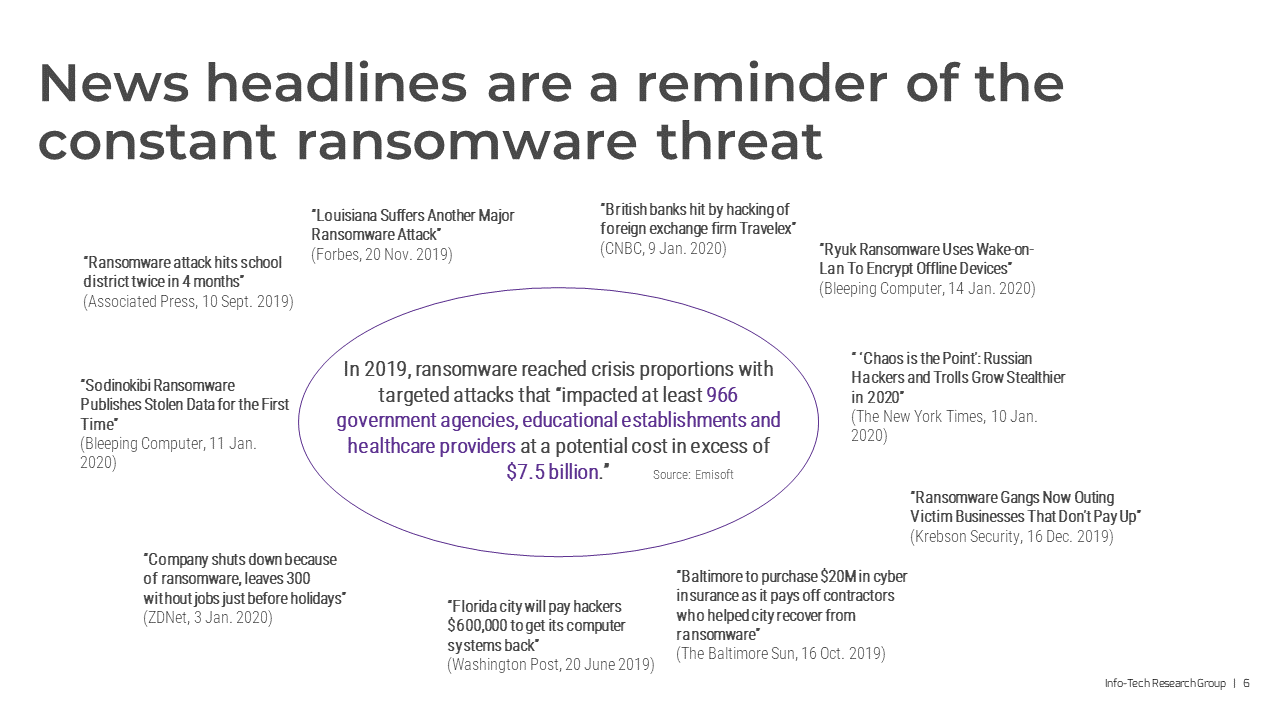
Before heading out of the office on leave, I wrote an article looking at “pay” or “not pay” the ransom:
When your technical defences fail – CyberAwake
I have written about how to defend your cybersecurity when your firewalls, anti-virus and other defences fail you: