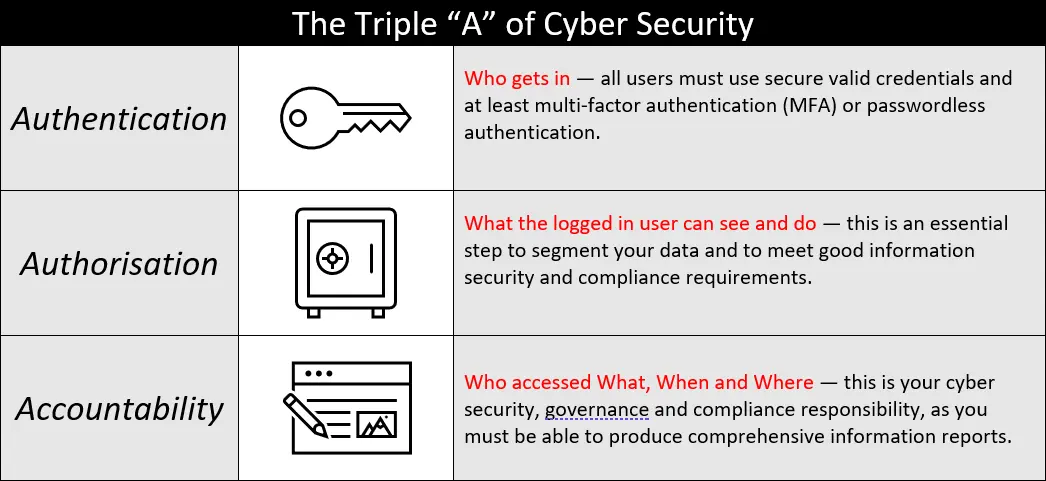
AAA = Authentication, Authorisation and Accountability AAA is a vital step in any cyber security strategy is: AAA, the first two As gives you the ability to control who has access to your information and what information they are able to see. The third A is accountability – without this …
End of support…
Software and hardware does have a use by date. Even though the equipment or software may still appear serviceable, if the vendor stops supplying updates, then the threat actors will start looking for vulnerable unsupported targets. Martin has written about this over on the Octagon Blog this month: Older versions …
JLR Cyber Attack
What is the impact of a well orchestrated cyber attack on a major organisation and it’s supply chain and associated businesses? In the case of the Jaguar Land Rover cyber attack it has been estimated that 250,000 jobs have been put at risk. Jaguar Land Rover: Some suppliers ‘face bankruptcy’ …
Jaguar Land Rover change their mind, of course…
Read this for what I had to say when JLR first announced they had suffered a cyber-attack: Jaguar Land Rover Cyber-attack | Smart Thinking Solutions Now they have changed their mind and they have discovered that some data may have been stolen: Jaguar Land Rover admits hackers may have taken …
Continue reading “Jaguar Land Rover change their mind, of course…”
What happens if you do not pay?
I have recently added a number of articles to my Ransomware Primer and as I am away on a project for a client, I thought for this week’s Wednesday Bit, I would point you at that primer: Your Takeaway The new to remind you how serious ransomware can be have …