I have been covering identity, credentials and authentication in our Summer webinar series – if you have not registered to attand it is not too late, as registration will also give you access to the recordings of the webinars you have missed. Digital identity and proving who you are is …
Phishing Attacks
It would have been difficult to miss the fact that Marks and Spencer, the Co-Op and Harrods have all suffered serious cyber-attacks recently. There has been speculation that the attacks originated from a phishing attack, as the hacking group DragonForce bragged in an email that they had hacked an employee …
Credentials Matter
As part of the Cyber Security Awareness Training I deliver, I always emphasise that any credentials people are entrusted with have a value and should be protected accordingly. Here is the proof of that statement – credentials for sale: ‘Russian Market’ emerges as a go-to shop for stolen credentials – …
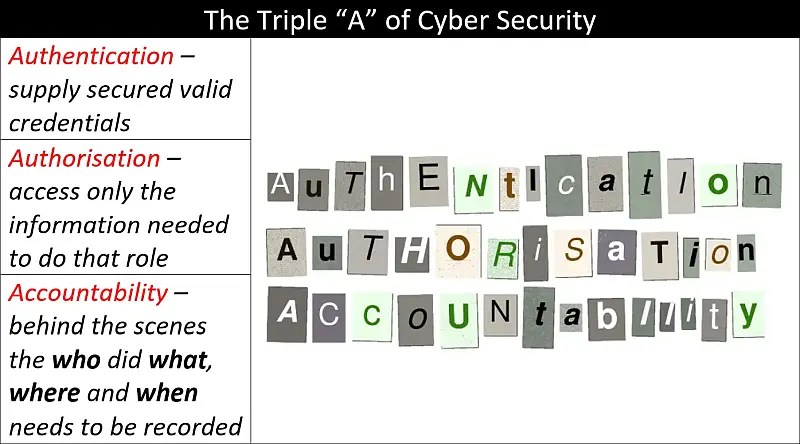
Authentication, Authorisation and Accountability – A Primer
Authentication, Authorisation and Accountability (AAA) and The Principle of Least Privilege (PoLP) come together in this primer to give you a basic understanding of the importance of knowing who is accessing your information and how much they can access. Another important idea covered here is what happens when something goes …
Continue reading “Authentication, Authorisation and Accountability – A Primer”
The Principle of Least Privilege – A Primer
Understanding the principle of least privilege – and then applying it in your organisation – is a fundamental step towards better cyber security. To help you gain the underpinning knowledge as to why this is important, I have written the following two articles: What the “Principle of Least Privilege” does …
Continue reading “The Principle of Least Privilege – A Primer”