In case you missed the memo passwords are important. Storing them in plain text where threat actors can eventually get access to them is a really bad thing. Misconfigured Firebase instances leaked 19 million plaintext passwords (bleepingcomputer.com) It is even worse if those passwords are associated with other sensitive information, …
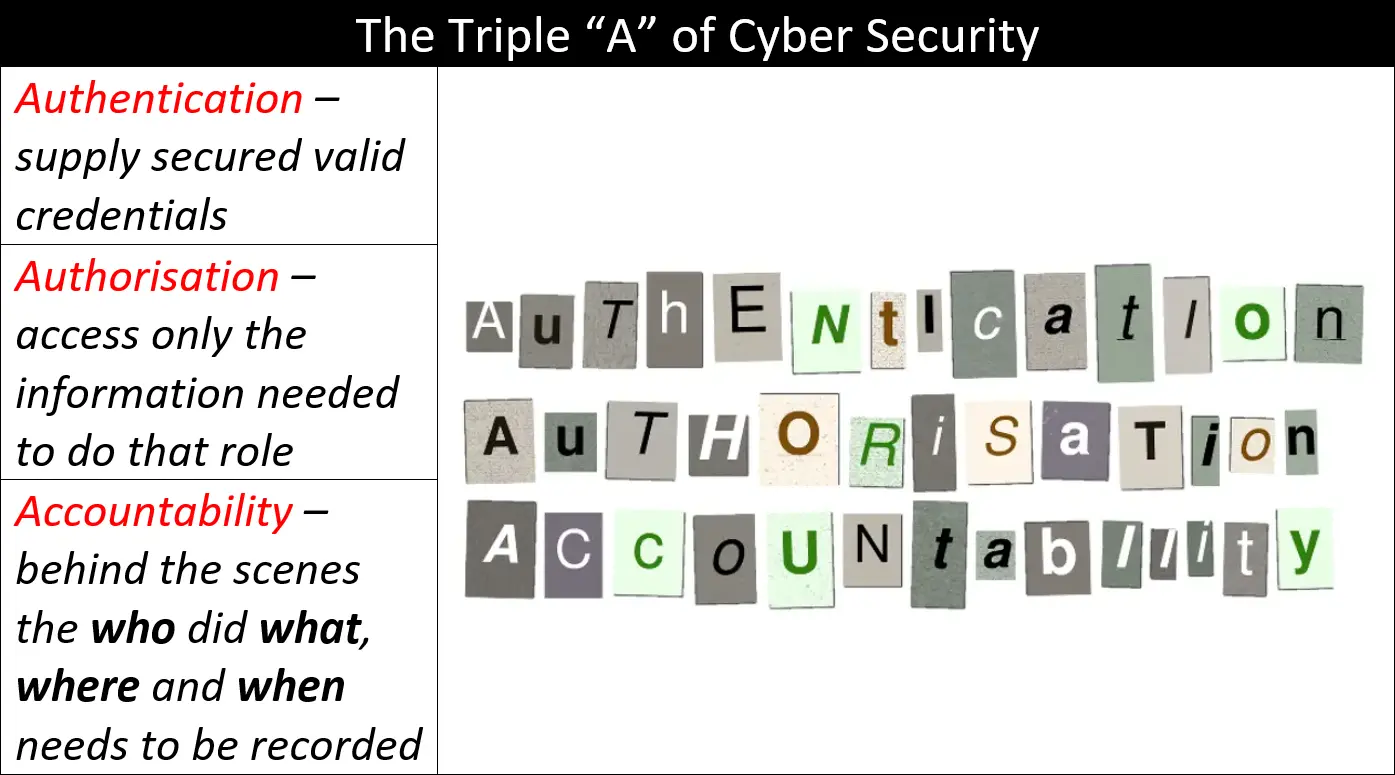
Why the “Principle of Least Privilege” works and something for free…
The Principle of Least Privilege (PoLP) is a fundamental concept in cybersecurity. It ensures that users are granted only the minimum necessary access rights required to perform their job functions. This principle is one I always enforce in cyber security as it is a powerful way of defending the most …
Continue reading “Why the “Principle of Least Privilege” works and something for free…”
“View Document”
Sometimes a cyber-attack is something as easy as adding a button saying “view document” when whale phishing senior people in an organisation. Ongoing Microsoft Azure account hijacking campaign targets executives (bleepingcomputer.com) Your takeaway When was the last time you audited the credentials and associated authorisations of those credentials? If you …
Back to passwords. Again!
It looks like I cannot get away from articles about passwords, which is not really a bad thing as passwords are still fundamental to everyone’s cyber security. I often read in the cyber security technical press that cyber attacks on even the biggest organisations start with the compromise of a …
We have done passwords, now let’s do MFA
Following on from the Back-to-Basics Password Primer mini-series – my latest article on CyberAwake is discussing the basics of multi-factor authentication (MFA): Back to Basics – MFA – CyberAwake In the next part I am going to discuss some of the weaknesses in MFA as a cyber security tool. Back …