Many business owners are uncertain about what is involved in an IT and Cyber Security Audit or whether it is even necessary, particularly if their business is small. Value for money is crucial, and an audit can seem expensive. However, no business is too small to be a target for …
Over-sharing
I have many discussions with clients about this topic – over-sharing. Whether it is in their social media, on their website or even on the notice board in the reception area. These snippets of information that are readily available without “hacking” are called OSINT – open source intelligence. The Internet …
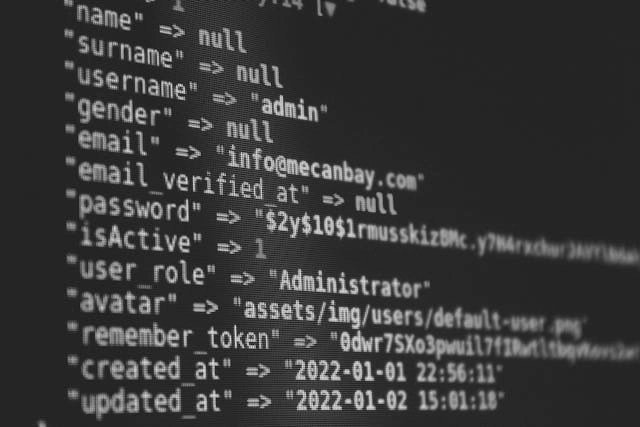
WordPress Again
As part of an ongoing IT and Cyber Security Audit, I had several meetings this week to advise a client on how to migrate their current bespoke website to WordPress. These meetings included how to find a good WordPress developer and the standard of cyber security they should demand for …
If you use WordPress then read on…
Automattic likes to tell us that it’s product WordPress is the world’s most popular website platform so it is dissapoibnting that a vulnerability has existed in it’s own popular plugin Jetpack since 2016. Jetpack fixes critical information disclosure flaw existing since 2016 (bleepingcomputer.com) How popular is Jetpack? As it offers …
Cloud Computing Cyber Security
Here is an excellent article from The Conversation, by Amro Al-Said Ahmad, looking at the vulnerabilities of cloud computing and infrastructure. How we’re using ‘chaos engineering’ to make cloud computing less vulnerable to cyber attacks (theconversation.com) Your Takeaway Many times, when I am involved with an IT and Cyber Security …