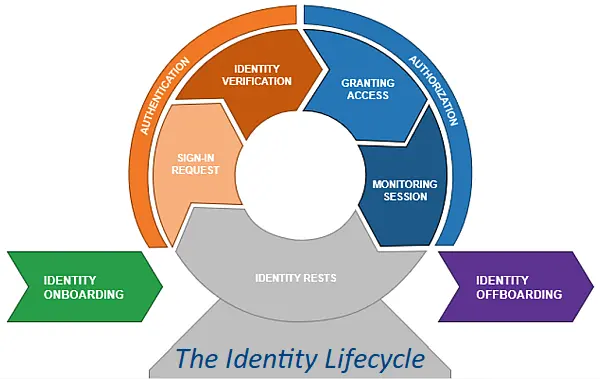
Today I am going to look at why credentials are so important in cyber security? Credentials for identity The management of credentials across your organisation for all services is an important impact of your cyber security, whether it is someone using the global administrator account as their “daily driver” work …
Authentication – Who Do You Let In?
Authentication, Authorisation and Accountability. This is the first part of a three-part series looking at the basics of the cyber security principle of “AAA”. Today we will start with Authentication It seems the easiest of principles. Everyone needs a username and password (credentials) to access any of your organisation’s systems. …
Risk Analysis – How to eat a very large quadruped!
Today we are going to look at the very first meeting I have with clients where we look at risk analysis. This is not a blog about eating an elephant – that is a figure of speech – although I do have a book that includes a paragraph or two …
Continue reading “Risk Analysis – How to eat a very large quadruped!”
Realistic Cyber Security
As you probably know, if you follow this blog, I was in Edinburgh last week at the 6th Intl. Conference on Big Data, Cybersecurity & Critical Infrastructure held at the Craiglockhart Campus, Edinburgh Napier University. For my post this week I wanted to share one positive thing I got from …
Building on your BitLocker Cyber Security
A follow-on from last week’s article by Ben about Windows BitLocker encryption – BitLocker for Cyber Security. BitLocker for full disk encryption As Ben described, Windows BitLocker is a feature that encrypts your entire drive to protect your data from unauthorized access or theft. It is available on certain versions …
Continue reading “Building on your BitLocker Cyber Security”