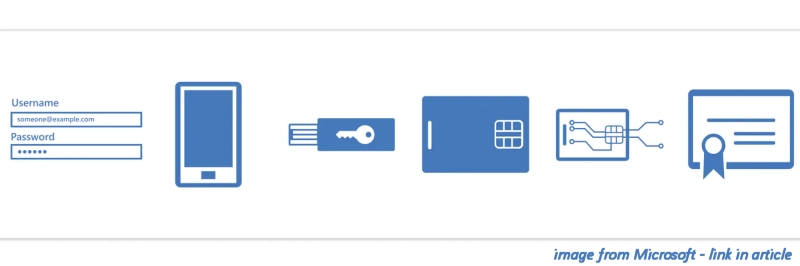
Whatever you read here in a few moments – it is my opinion that MFA (Multi-factor authentication) still remains a key tool in protecting your team’s credentials and defending your information. MFA under attack There have always been weaknesses in and attacks against, some very simple such as just annoying …
Back to Basics – The Collection.
This week the Wednesday Bit is about is highlighting some of the mini-series and back to basics cyber security primers I have written. Why? Because yesterday when I was speaking with a long-term client about password hygiene in their organisation, they were unaware I had a Password Primer they could …
Phone number recycling
Here is something new to think about: Meta brushes off risk of account theft via number recycling • The Register I must admit I had never thought about this type of leak in a cyber security plan. I am not sure how relevant this is in the UK, but it …
If Microsoft can get it wrong…
It has emerged that senior executives at Microsoft had their emails hacked and monitored by Russian threat actors for nearly 2 months. Microsoft network breached through password-spraying by Russian-state hackers | Ars Technica The attack was not sophisticated. The threat actors – Midnight Blizzard – using nothing more than a …
Unsolicited MFA prompts
Last Wednesday I published my MFA Primer series and part two looks at this type of cyber attack against multi-factor authentication. In brief when the threat actors have a valid set of credentials they repeatedly try and access the service with them, generating multiple MFA requests to your authenticator app. …