I like Signal as a secure, private messaging app and if your business needs an unaccountable way of communicating then I recommend Signal. Now Signal is starting to offer a secure encrypted back-up service for your messages: Signal adds secure cloud backups to save and restore chats – BleepingComputer The …
Credentials Matter
As part of the Cyber Security Awareness Training I deliver, I always emphasise that any credentials people are entrusted with have a value and should be protected accordingly. Here is the proof of that statement – credentials for sale: ‘Russian Market’ emerges as a go-to shop for stolen credentials – …
Deepfake
The stakes can be high when threat actors invest the time and money into creating deepfake videos to hack an organisation, here an example from last year: You may not have $25m in your bank account but here is the state of play of deepfake hacking So tools that can …
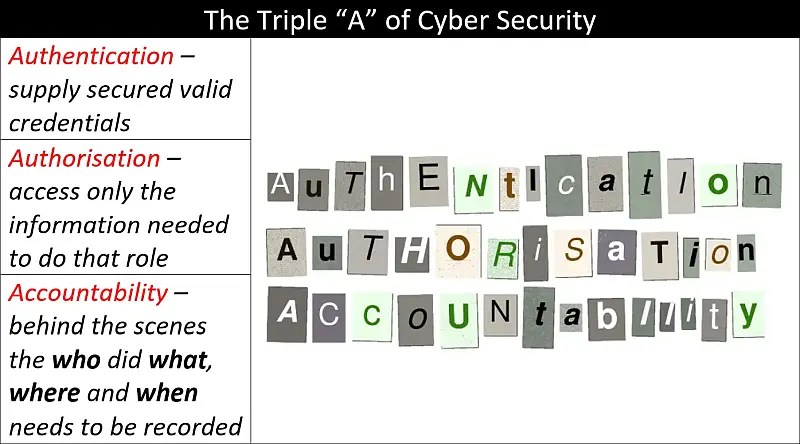
Authentication, Authorisation and Accountability – A Primer
Authentication, Authorisation and Accountability (AAA) and The Principle of Least Privilege (PoLP) come together in this primer to give you a basic understanding of the importance of knowing who is accessing your information and how much they can access. Another important idea covered here is what happens when something goes …
Continue reading “Authentication, Authorisation and Accountability – A Primer”
Signalgate
I am not sure anyone is actually calling it that… We have all seen and or heard of this story that is running in the US and around the world: Trump and intelligence chiefs play down Signal group chat leak – BBC News I am not going to get into …