Having read Ben’s article on Phishing Email, this morning, before posting it to Smart Thinking as part of my Back-to-Basics Email Phishing Primer, I was reminded of a Bruce Schneier article and associated research paper I read last week – looking at how anyone can end up following a misleading …
Email Phishing Primer
We have a guest writer for the next part of the Email Phishing Primer. Ben one of the support team at Octagon Technology has written about this cyber security threat from his point of view as someone who must advise clients on this issue on a day-to-day basis. Part eight …
Phishing Attacks – It is in the numbers. (pt 6)
I think we have established two key points in previous articles in this Back-to-Basics, Email Phishing Primer: 1 – Threat actors’ primary motivation for sending out phishing emails is financial. 2 – One of the best tactics any organisation can use to defend against phishing attacks is cyber security awareness …
Continue reading “Phishing Attacks – It is in the numbers. (pt 6)”
Credentials are King
Threat actors are always looking for good sources of valid (stolen) email and password combinations – and there are many hundreds of millions available to them. 361 million stolen accounts leaked on Telegram added to HIBP (bleepingcomputer.com) Once they have these credentials, the threat actors will be trying them out …
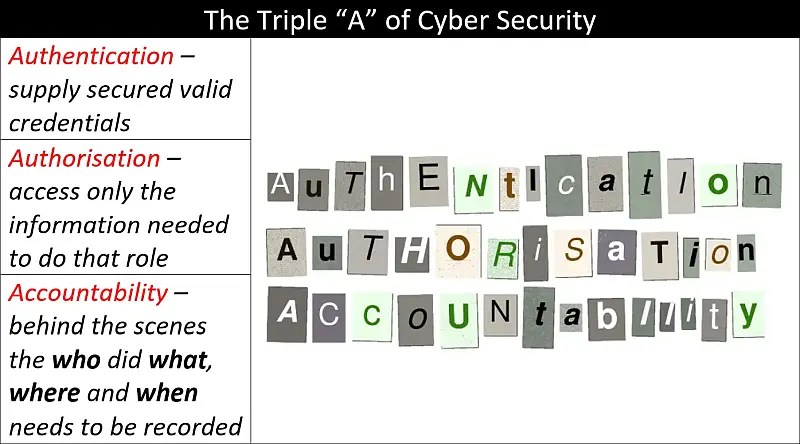
The Principle of Least Privilege and Authentication, Authorisation and Accountability – A Primer
Authentication, Authorisation and Accountability (AAA) and The Principle of Least Privilege (PoLP) come together in this primer to give you a basic understanding of the importance of knowing who is accessing your information and how much they can access. Another important idea covered here is what happens when something goes …