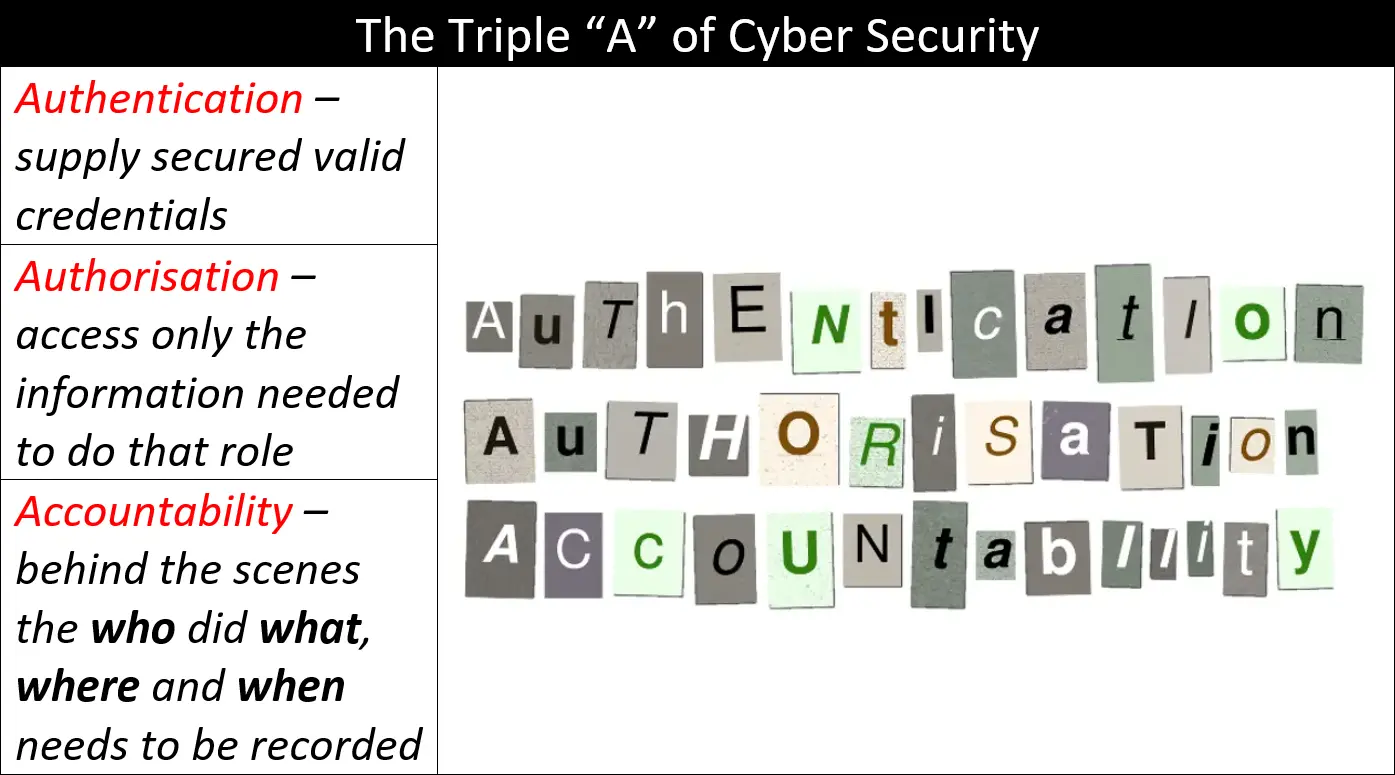
This article follows on from last week’s Why the “Principle of Least Privilege” works and something for free…. If you want the something for free, then you had better read that article first! Let’s start with a simple definition. The Principle of Least Privilege (PoLP) is a fundamental concept in …
Continue reading “What the “Principle of Least Privilege” does for you? (pt. 1)”