This week I have been discussing user and systems monitoring with a client’s senior management team. Their immediate response was that they did not want to spy on their staff as they trusted them – and to be fair they are appear to be a friendly supportive organisation. However my …
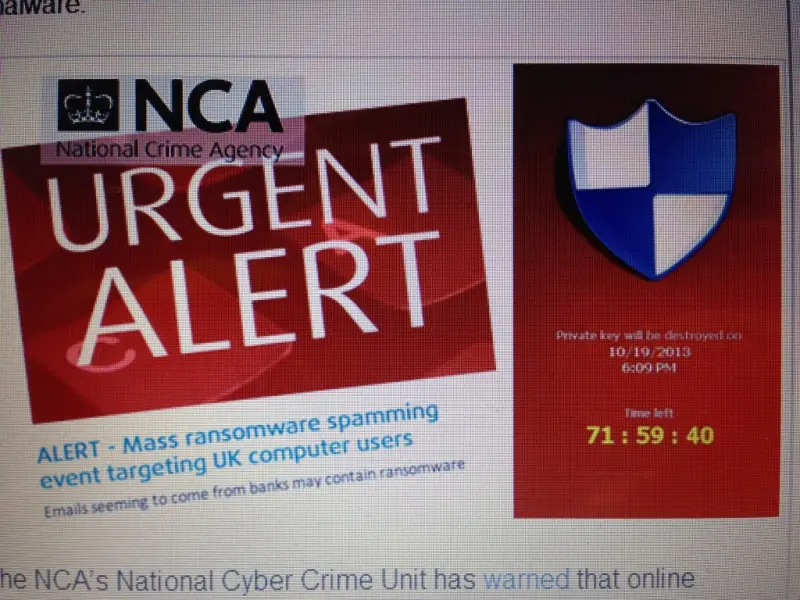
Just Ransomware!
Having ended last week’s cyber security news with ransomware stories and then starting this week’s news again with ransomware, our Operations Manager Martin and I ended up talking about the first time he and I dealt with this type of malware on a client’s network and in-house server… Ransomware in …
Apple MacOS Malware
Once upon a time I would be lectured by Mac users on how Macs did not get malware or computer viruses. This was probably because the user base was not big enough to attract threat actors. Today however things are very different. Macs are as vulnerable as any other computer …
Zero-day Google Chrome vulnerability
Emergency patches have been issued for Google Chrome to address a vulnerability that is being exploited in the wild. Google fixes another Chrome zero-day bug exploited in attacks (bleepingcomputer.com) If your team uses Chrome then check these patches have been done. We use Google Chrome and we know our patching …
Octagon Technology’s Security Operations Centre is Online
Our Security Operations Centre (SOC) is now operational and our first clients are already benefiting from our continuous 24/7 monitoring, analysis, alert and response service. You could as well… Why you need a Security Operations Centre Here is a great quote from the director of the Security Operations Centre: A …
Continue reading “Octagon Technology’s Security Operations Centre is Online”