When I am delivering the cyber awareness training – and people relax, realising I really mean it when I say there are no stupid questions – I often get asked “how do I know if my computer was infected?”. Usually just before being asked about the length of a piece …
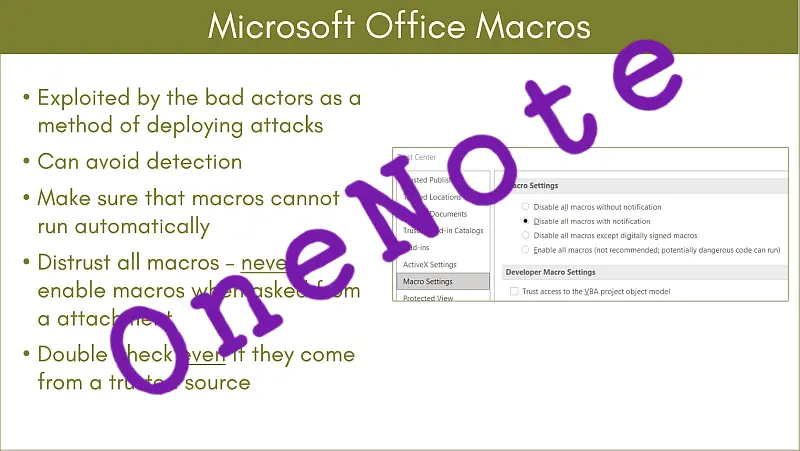
OneNote – the threat actors new best friend…
Once it had been discovered how straightforward it is to obscure a malicious package inside a OneNote .one attachment and mixed with “something new”, that users may not have seen before, it was obvious that the use of .one attachments for the delivery of malware was going to go up. …
Continue reading “OneNote – the threat actors new best friend…”
The thefts have started – The SVB collapse…
Following my article earlier this week to warn you to be on the look out for scams – theft attempts – based around the collapse of the Silicon Valley Bank (SVB), Bleeping Computer is reporting that the cybercriminals are actively exploiting the situation looking to steal money and data: Cybercriminals …
Continue reading “The thefts have started – The SVB collapse…”
One of the top cyber security threats has some new tricks
The Emotet botnet comes and goes, but it is still one of the top cyber security threats active today. Its flexibility and updates have kept it in use by threat actors whilst other malware has been defeated by cyber security defences. The latest versions are still arriving in phishing emails, …
Continue reading “One of the top cyber security threats has some new tricks”
OneNote enhanced security is coming…
Following the recent increase in cyber attacks using Microsoft OneNote .one attachments as the carrier, OneNote is to get some enhanced security updates from Microsoft. Although it looks like we will have to wait for this extra protection from high risk phishing attacks until the end of April 2023. Microsoft …