Yesterday I published an article on CyberAwake discussing the advice every security expert gives (including myself) “don’t click on that link”. Don’t blame your team “Just Click Here” – CyberAwake It’s more complicated than you would expect.
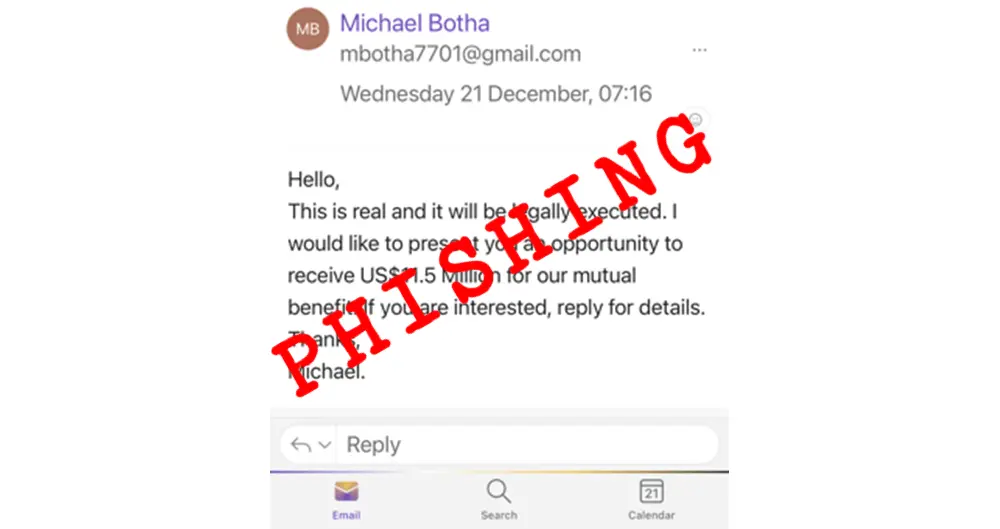
Sometimes a scam is obvious…
…but sometimes you do get fooled. Today I have published my first cyber security article, of 2023, over on our online training site CyberAwake. It is about a spam email that got through our email defences. Sometimes a simple email may work for the bad guys – CyberAwake Here is …
One more warning about online shopping and scam adverts
the FBI have issued a warning about fraudulent adverts taken out by threat actors and displayed on legitimate search engine requests. The FBI is warning the public that cyber criminals are using search engine advertisement services to impersonate brands and direct users to malicious sites that host ransomware and steal …
Continue reading “One more warning about online shopping and scam adverts”
Phishing Infographic
The US government Cybersecurity and Infrastructure Security Agency (CISA) recently released an useful infographic highlighting many aspects of phishing cyber attacks: Phishing Infographic (cisa.gov) It also includes some good advice on how to deal with the threat.
Some Seasonal Training over on CyberAwake
Just in time for Christmas – I have an article, published yesterday, over on our inline training site, CyberAwake, with a few tips on tightening your cyber security before heading off for your Christmas break. Christmas cyber security advice – CyberAwake In particular I offer some advice on controlling that …
Continue reading “Some Seasonal Training over on CyberAwake”