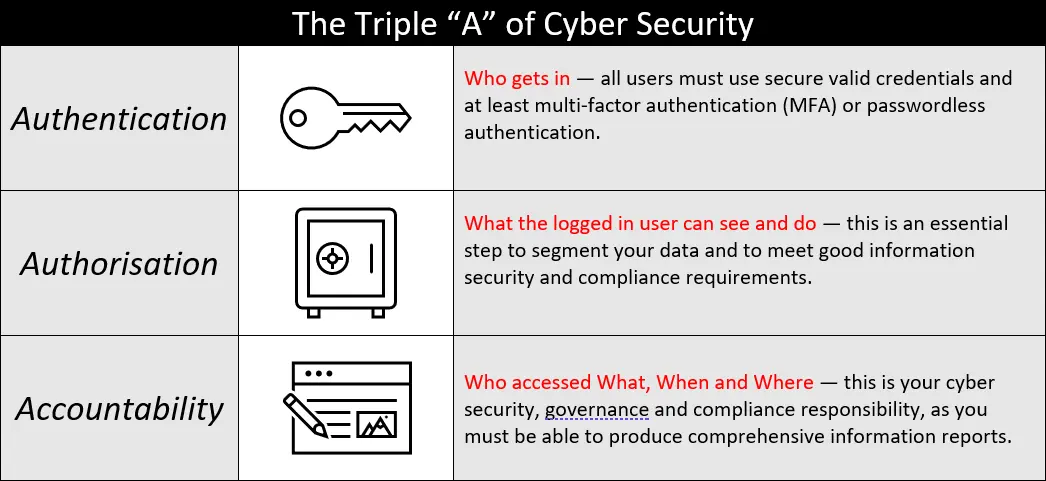
AAA = Authentication, Authorisation and Accountability AAA is a vital step in any cyber security strategy is: AAA, the first two As gives you the ability to control who has access to your information and what information they are able to see. The third A is accountability – without this …
What happens if you do not pay?
I have recently added a number of articles to my Ransomware Primer and as I am away on a project for a client, I thought for this week’s Wednesday Bit, I would point you at that primer: Your Takeaway The new to remind you how serious ransomware can be have …
Back to Basics – Why MFA? (pt.3)
In this third part of my MFA mini-series, I am going to look at some of the resistance that we get when trying to implement multi-factor authentication. MFA – It is like medicine that tastes bad In the first part of this series, I briefly explained the highlights of why …
Ransomware the Next Steps (pt.2)
In the first part of this article on how ransomware has changed, we looked at the actual attacks, today we are going to look at ransomware payments. Ransomware. Pay up? In the early days of ransomware, paying for the decryption key was an option. Although back then most people who …
Ransomware the Next Steps (pt.1)
Ransomware is probably the most well known of the modern cyber security threats, regularly making the mainstream press when high profile organisations and/or large numbers of users are compromised by the actions of cyber-criminals (BBC News, 2025). When ransomware began… I can remember the first time we had to deal …