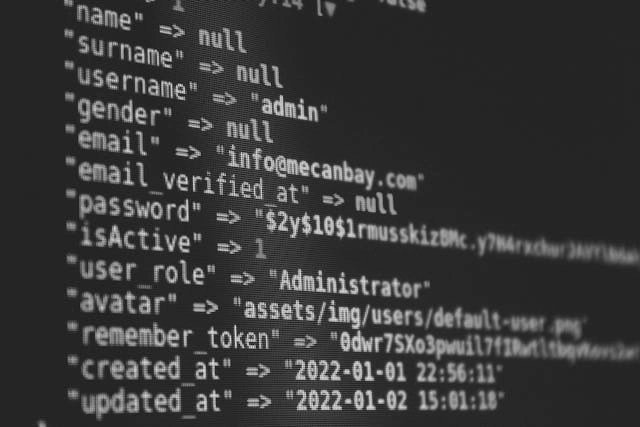
Many business owners are uncertain about what is involved in an IT and Cyber Security Audit or whether it is even necessary, particularly if their business is small. Value for money is crucial, and an audit can seem expensive. However, no business is too small to be a target for …
Your BYOD Policy – What? (pt.5)
Are you still onboard with Bring-Your-Own-Device (BYOD) as a tool to improve your organisation’s productivity and help make your team “happier”? Then today, I am going to give you something harder to think about. BYOD and Your Information Allowing one of your team to work on their own laptop is …
Your BYOD Policy – Where do you start? (pt.4)
I discuss policies with clients a lot. This includes just asking to see them when I start an IT and Cyber Security Audit or when I am booked to deliver some Cyber Security Awareness Training. I am never surprised when they do not exist or possibly even worse, “not fit …
Continue reading “Your BYOD Policy – Where do you start? (pt.4)”
A Real-World Example – BYOD A Primer (pt.3)
I did promise you that today I would make a start on what a BYOD (Bring-Your-Own-Device) policy would look like. However, regular readers will know I can get distracted easily… The distraction this time came from one of our members of staff who reminded me that we developed a BYOD …
Continue reading “A Real-World Example – BYOD A Primer (pt.3)”
BYOD – Where do you start? (pt.2)
After a short wait… (Another thing about phishing emails… (pt.12) and Problems with QR Codes here is the second part of my series on BYOD – Bring-Your-Own-Device. Trust and BYOD If you are or are thinking of allowing your team to use their devices to do your work – then …