The rise of hacking-as-a-service, complete with support, updates (to evade detection) and user feedback and testimonials has seen an increase of less Technal threat groups being able to launch effective phishing attack. The malware, Mystic Stealer can be rented on the dark web for as little as $150 per month. …
Why team training has to be part of your cyber security plan?
We all have the best technical cyber security defences in place we can afford (or we should have). The threat actors know this so they are always on the hunt for those techniques that our anti-virus and filtering systems cannot detect. PowerShell is a powerful Windows command line and automation …
Continue reading “Why team training has to be part of your cyber security plan?”
Explain to me what a phishing email looks like?
This is something I try and explain at every cyber security awareness session I run – what is a phishing email? The answer is constantly changing as the threat actors never stand still in their attempts to get us to infect our own computers. I used to point to bad …
Continue reading “Explain to me what a phishing email looks like?”
New info stealing malware
Bandit Stealer malware is promoted by the hacker developers as the most advanced information stealer available to threat actors. It can exfiltrate data from most popular browsers including usernames and cookies and other system information such as IP addresses and details of a victim’s computer. The Telegram messaging app is …
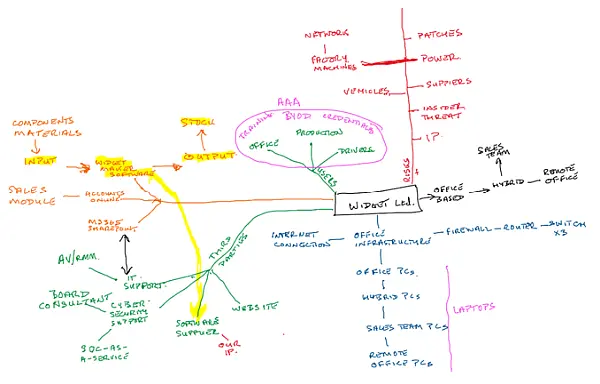
Risk, Risk, Risk
Following a meeting with a client last week and the first news item I posted on Monday, I started this week thinking about risk, which has led to a short series of articles looking at… risk! On Smart Thinking I wrote about risk analysis and how I get started with …