This is a continuation of last week’s article that looked at stealth malware infection from a malicious phishing email. Phishing Emails I spend a lot of my time writing and talking about malicious phishing emails. It is the easiest attack vector into your organisation that a threat actor has access …
Extortion Ransomware
I have a couple of articles over on CyberAwake looking at the issue of extortion ransomware and offering some tips for small and medium organisations on how to protect their information using tools they already have. From Encryption Ransomware To Extortion Ransomware Part I From Encryption Ransomware to Extortion Ransomware …
Windows 11 to get extra phishing protection
This is only being released to the Windows Insider programme at the moment but if it is will get to the general release soon. Windows 11 gets phishing protection boost and SHA-3 support (bleepingcomputer.com) It is designed to protect your credentials, alerting you if you are about to carry out …
Continue reading “Windows 11 to get extra phishing protection”
Infected and you didn’t even know it…
When I am delivering the cyber awareness training – and people relax, realising I really mean it when I say there are no stupid questions – I often get asked “how do I know if my computer was infected?”. Usually just before being asked about the length of a piece …
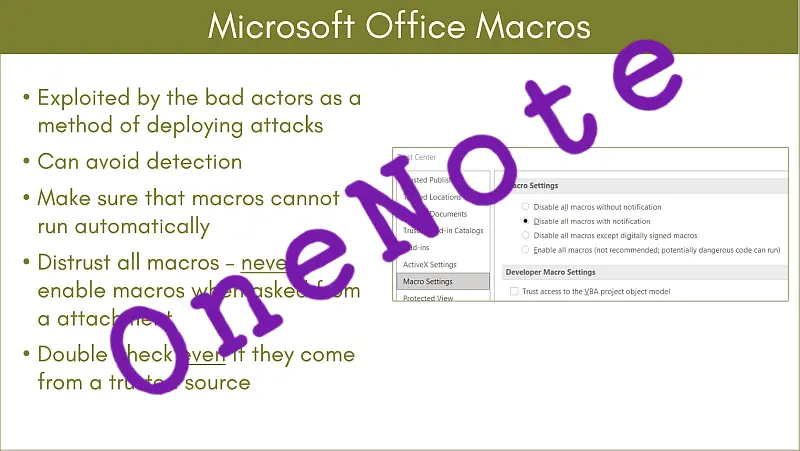
OneNote – the threat actors new best friend…
Once it had been discovered how straightforward it is to obscure a malicious package inside a OneNote .one attachment and mixed with “something new”, that users may not have seen before, it was obvious that the use of .one attachments for the delivery of malware was going to go up. …
Continue reading “OneNote – the threat actors new best friend…”