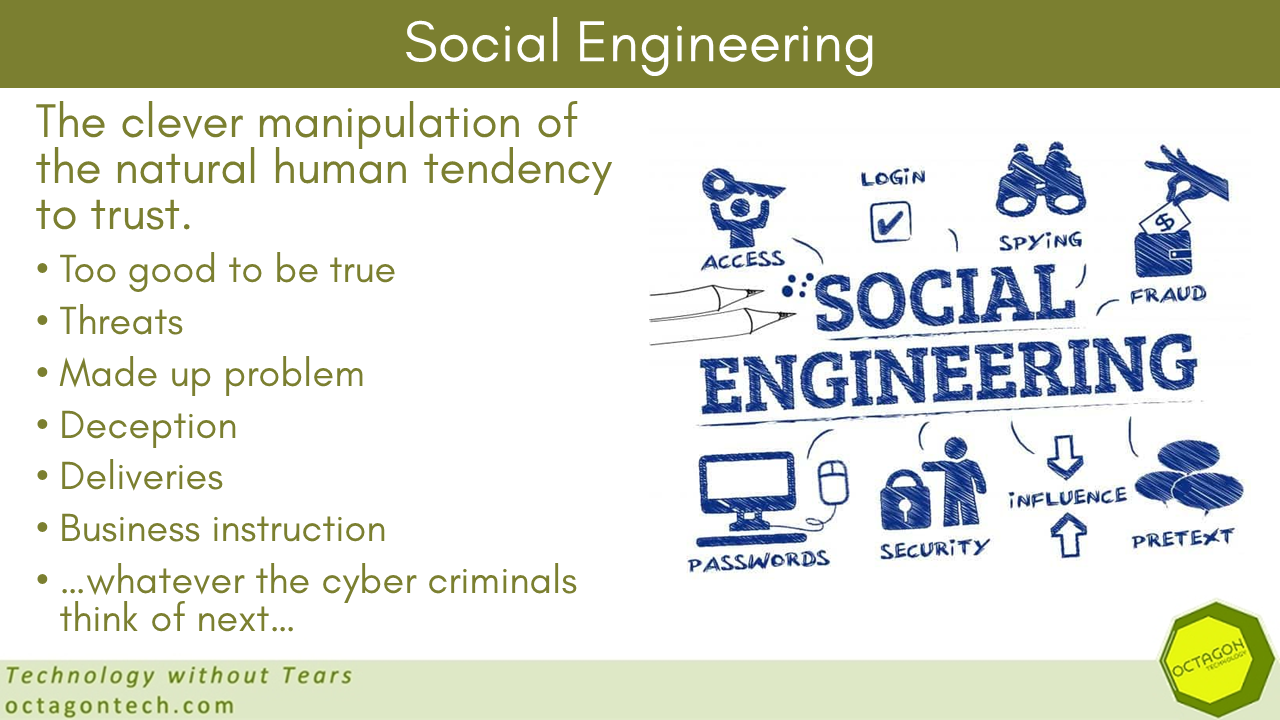
The penultimate part of my mini-series looking at Ransomware has been published today on CyberAwake: Before – Ransomware Part 9 – CyberAwake Here are the rest of the parts – published across Smart Thinking, CyberAwake and Octagon Technology. Ransomware Mini-Series (2023) Ransomware: Is it a Threat? (Part 1) A Bag …
Continue reading “The Ransomware mini-series is almost complete”