This is the 1000th news feed post here at Smart Thinking, so I was told by Marketing I needed to do something special. I would have simply gone on reporting the stories of the day and giving out advice, making sure you are all provided with a range of cyber security news to help improve your security stance. However, marketing rules, here is post 1000… my way.
The start
The way we tell the cyber security story here at Smart Thinking has come a long way since we put our first post up:
EasyJet admits hack – Smart Thinking Solutions
I was not sure how this site was going to develop then, posts were not daily, as they are now but I had been inspired to produce a cyber security information site, for businesses and organisations, during my degree studies, by such sites as Bruce Schneier and SANS Internet Storm Centre.
I really feel it would improve people’s cyber security, my sharing cyber security advice and stories and trying to get businesses and organisations to understand the scale of the threat actors out there that could have a serious impact on their operations. I thought by giving context to stories in the media, illustrating how these could impact them, providing links to the source material and other resources, and giving advice they could understand and get to grips with, people would avoid the “rabbit in the headlights” reaction and feel that the solutions were within their grasp.
Because It’s Friday
However once I started posting daily one thing soon struck me and the readers – “who wants to visit a website that only writes about doom and gloom?”.
It cannot all be serious… #BeCyberSmart
Then Kamila over on Octagon ran this post:
Why do I celebrate World Octopus Day? – Octagon Technology
Which allowed me to reference my inspiration, Bruce Schneier who has a thing about squid:
We did not have the “Because It’s Friday” theme in the early days of the feature. I think this was the first time we used it, and it stuck and it has become a very popular weekly post:
Because it is Friday… The Space Race
Space, artificial intelligence, flying cars, Dilbert and xkcd are frequent subjects of our Friday diversions.
Over the Queen’s Platinum Jubilee weekend we ran a series of special posts looking at technology from 1952 and how it has influenced technology in 2022.
Technology and the Platinum Jubilee
I am sure some people return on Fridays just to see what odd things turn up.
Then we got the Weekend Read
Sometimes a story is too big, complicated or not exactly on topic. Monday to Friday 9 to 5 people do not have the time to read these types of post, even though the background information or underpinning knowledge would be useful to them – that’s why we now have the “Weekend Read” feature.
The stories we have covered are varied and are include podcasts and videos:
Machine learning is vulnerable to a wide variety of attacks
Public Interest Technologist (Bruce Schneier YouTube video)
With a title that includes “Bond Villains” you cannot possibly miss reading this…
More things to think about when it comes to AI
My top ten cyber security posts
So here, (at last some may say), is the cyber security blog post I was asked to write by Marketing – my top ten posts out of the 1000 we have written. They are in no order of ranking, it is just how I looked them up, but there is a nod to Randall Munroe and of course, there are more than ten!
These had to be “hard cyber security” articles, none of the humour of “Because It’s Friday” or side journeys of the “Weekend Read”, so do not be deceived by the titles. Have a read and learn something new about cyber security.
1
I am not the only person who contributes to Smart Thinking – Diana has written the occasional piece:
Cryptography after the aliens land (another post that includes Bruce Schneier)
Diana was the driving force behind the BeCyberSmart feature we ran – here are a few gems from it:
Hallowe’en and maybe the hacker god will return from the dead! – #BeCyberSmart
The Tale of Marconi and the Ethical Hacker – #BeCyberSmart
I just have to use my slippery fish analogy again… – #BeCyberSmart
10
Diana gets another entry – just because she used a quote from Dad’s Army and linked it to cyber security.
11
Ransomware is one of the biggest threats to any organisation’s information systems – large or small (do you have a cyber attack secure backup?). Ransomware attacks are rich picking for both the multinational, highly skilled, organised gangs and now the smaller gangs are getting in on the action with Ransomware-as-a-Service.
Knowledge of the current state of ransomware is an essential step in everyone’s cyber security plan
100
Because business-like organisational skills are being used in ransomware campaigns, the term RansomwareOps is starting to be used more often to describe the way ransomware gangs operate.
Now the ransomware gangs are offering bug bounties
101
But to suffer the problems of ransomware your systems have to be infected – somehow…
How the threat actors can get ransomware onto your systems
110
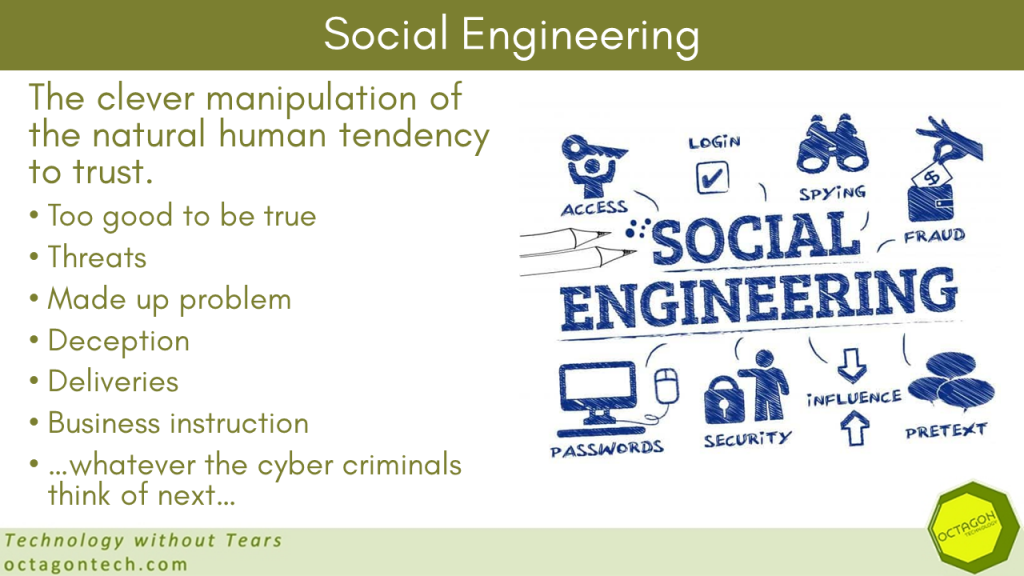
The most common way threat actors get malware into organisations is by using phishing with social engineering techniques and email:
“Of the 39% of UK businesses who identified an attack, the most common threat vector was phishing attempts (83%).”
Cyber Security Breaches Survey 2022 (UK Government. 2022)
Email scams – how hard is it to spot them?
This is very important so here are a couple more posts on the subject:
Phishing email alert – Excel spreadsheets loaded with RATs
111
I run articles based on academic papers and research, that show what may be the cyber security threats of the near future:
Samsung smartphones with leaky security
1000
I go back to articles and update them as a story develops – often it means you get to see the fix to the problem raised in first post – but not in this case:
1001

Posts alert people to vulnerabilities in common (and sometime less common) software packages, updates and patches:
The update above did include the fix for the issue. Below is the advice we regularly post about updates and patches
My advice: Either you or your IT support need to check whether these issues impact your systems. You need to have a master document that details your systems, hardware, software, online, networks, back-ups, suppliers etc – so when cyber security (or operational) issues arise you and your support teams can quickly check if you are affected. From there you can take fast, effective action.
1010
Privacy is a big topic on the site. If you understand privacy and can operate a good privacy policy, then that will support an excellent cyber security plan.
Tor browser can now give privacy and evade censorship barriers
The other side of that discussion, is when privacy is eroded, particularly by governments, as our cyber security will suffer:
Smart Thinking Solutions supports this UK Government initiative:
Let’s stop abuse together – Stop Abuse Together (campaign.gov.uk)
I am sure I have missed many important posts that should have made this list – but they are all there if you to go and have a browse.
Get your Smart Thinking Solutions News in other places
Each week I write a Cyber Security Round-up for the Octagon Technology Blog.
From this Kamila sends out a Cyber Security email newsletter, each week, picking the six stories from Smart Thinking Solutions that she thinks are the most important – if you want to be included in that exclusive mail out, then let her know here.
We generate an (old fashioned) RSS feed, which several sites use to provide daily cyber security news on their sites:
Cyber security news | Cyber Awake Team Training
There are instructions in the blog post below, on how to access our RSS feed. If you use our daily news on your your site let me know you are using it and I will publicise your website.
This RSS feed can be used in Outlook, so your daily cyber security news will show up in it’s own folder whilst you process your email.
More to come…
If cyber security stops being a thing and the threat actors go off and raise organic chickens (!) or something, then we will transition Smart Thinking Solutions into a different type of company. Until that happens we will continue to bring you the news, advice and services that we think will improve your cyber security – with a little humour and light relief sprinkled around.
Clive Catton MSc (Cyber Security) – by-line and other articles
References
UK Government. (2022). Cyber Security Breaches Survey 2022. Retrieved July 9, 2022, from https://www.gov.uk/government/statistics/cyber-security-breaches-survey-2022/cyber-security-breaches-survey-2022
(I have been very keen that we not only use quality, respected news sources (which we link to so they get the credit and the traffic) but we also use primary sources and reference them – including, reports and academic papers. A range of sources will allow our readers to be better informed – better informed means better decisions.)
Further Reading
Scalable backup solutions for computers, Macs, laptops, servers, WordPress and cloud services
Another photo of my laptop screen – 1000 cyber security posts – Clive’s Blog (clivecatton.co.uk)
(I often post links, both internal and external, for readers to follow-up on or get background information on the topics discussed.)
Just one more thing…
For those of you to young to recognise the car in the photo above, it is a Morris Minor 1000.



