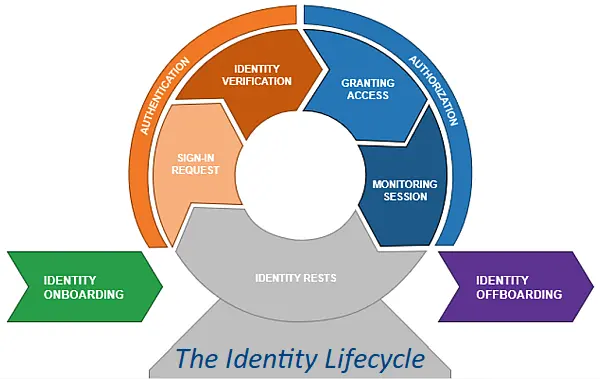
Authentication, Authorisation and Accountability. This is the first part of a three-part series looking at the basics of the cyber security principle of “AAA”.
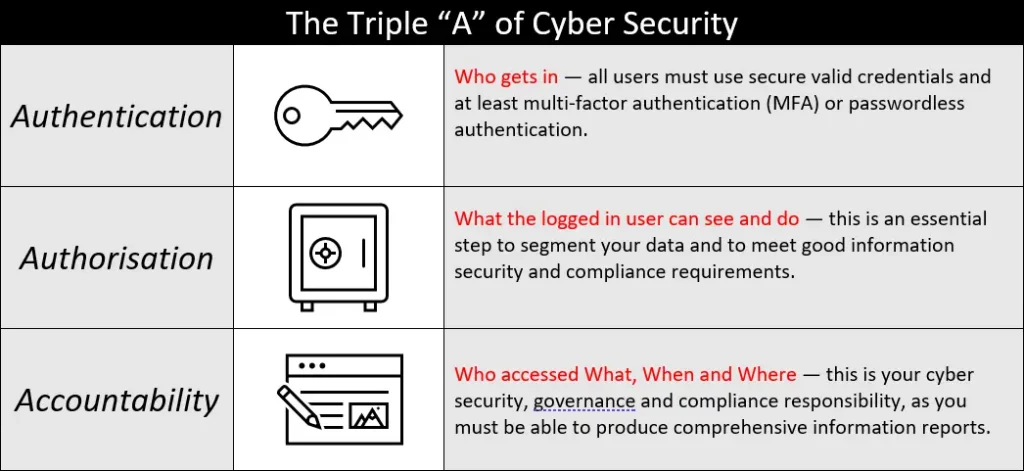
Today we will start with Authentication
It seems the easiest of principles. Everyone needs a username and password (credentials) to access any of your organisation’s systems. However, the management of these credentials is usually neglected or they are issued without a management decision. I cannot count the times I have discovered redundant credentials still live on a system, often with serious levels of access (that is a story for part 2).
Even after a major clean out, entropy soon sets in if someone is not given the express job of maintaining the credential health of an organisation.
We often take on that role for a client.
An Authentication Advantage
There is always someone who will have a case as to why they need a variation on the organisation’s authentication policy. When we manage the credentials for a client, it is easier for us to say no, than it is for a friend who works in HR or in many cases works in the accounts department! We still see the person who does the books in the role of IT manager, cyber security officer, credential manager…
One password and username – many users
Another variation of the credentials policy we often see is “one set of credentials many users”, this is not a good policy. Every user needs their own accountable set of credentials. (More about this in part 3).
Sometime specific users, often senior members of staff, need two or more sets of credentials so they can work securely – sometimes they have them, sometimes they do not. (More about this in part 2).
Multi-factor authentication (MFA) – a quick explanation
“Multi-factor authentication (MFA) is also referred to as dual-factor authentication (DFA) and two factor authentication (2FA). All have the same function – to provide a one-time password (OTP), securely and only to the authorised user, so they can get access to a service. Examples of services that implement MFA for added security are Microsoft 365, Google, WordPress and Amazon among many others.“
Again I still go into organisations where MFA is not implemented or if it is there will be exceptions. There is always an excuse – and it is those excuses that the threat actors love.
Use it.
Passwordless
Passwordless is one of the latest ways to secure credentials and therefore identity and authentication. Do away with the passwords and instead use a cryptographically secure personal authentication device to confirm it is you when you login. Sounds complex? It isn’t.
Most of us would use the Microsoft or Google Authenticator app on our phones as our personal secure key to get in.
What this article is not…
It is not a deep dive into the many ways you can securely manage identity in your organisation so only those who should can get in.
What this article is…
It is a start to make everyone realise how important it is to have effective secure identity management for every system in your organisation.
Next
Tomorrow Authorisation
Clive Catton MSc (Cyber Security) – by-line and other articles
The Series
Part 2 Authorisation – It Shows You Care.
Part 3 Accountability – It Shows You are Watching.