We finished last week with a ransomware story. let’s start this week with another:
BlackCat ransomware hits Azure Storage with Sphynx encryptor (bleepingcomputer.com)
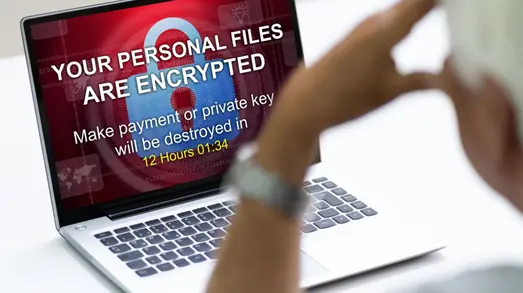
This ransomware story has a twist, the prolific BlackCat ransomware gang are ow using stolen Microsoft credentials in custom software to execute their attacks.
Your takeaway
You may not be a big player, but if a threat actor has compromised any of your Microsoft 365 (or Google Workspace) credentials, even you could be at risk. May be not from a ransomware attack, but just the simplest of business-email-compromise attacks.
Why take the chance – protect your organisation’s credentials. Not sure how to do that? Then get some help, read a book or a blog or contact us.
Back in the real world of small businesses
I am working with a client at the moment, who has no backup** – which is the most basic of ransomware steps – and no incident response plan for any incident, even though they worked through the lockdowns! Time to get it on paper.
Your Takeaway – more…
It hasn’t changed since Friday – click here for your takeaway.
Clive Catton MSc (Cyber Security) – by-line and other articles
** Backups are essential and before I have submitted the final audit report to the mentioned clients, our team has deployed some of our backup solutions as a temporary fix.

