I recently wrote a couple of articles looking at some real-world email phishing attacks aimed at me – the links are below. This article is about another that happened this past weekend.
Email Phishing Attack – The “wear you down” tactic.
One of the favourite tactics threat actors use is to “wear you down”, the constant repetition of an email, or MFA request to try and get you to forget your cyber security awareness training and click “yes” when you meant to click “no”.
This email phishing attack started on Friday evening at 18:51 to be precise, whilst I was watching Halo on the big screen in the sitting room. Diana was away for the weekend. To be honest I ignored the first few email alerts on my phone, however curiosity got the better of me – which is what the threat actors were hoping – and I had a look.
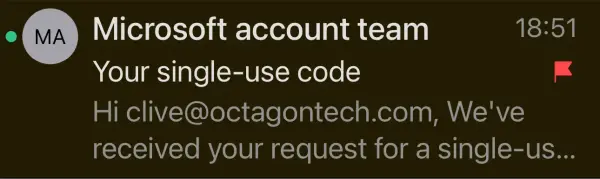
The email really did come from Microsoft, which is why it got through my “out of hours” email filter, but after a quick glance at the message I knew exactly what it was and went back to watching the Master Chief.
But the threat actors were persistent. The email alerts kept coming in all through the night until 6:11 in the morning, when eventually their computer gave up on me and moved onto another potential victim.
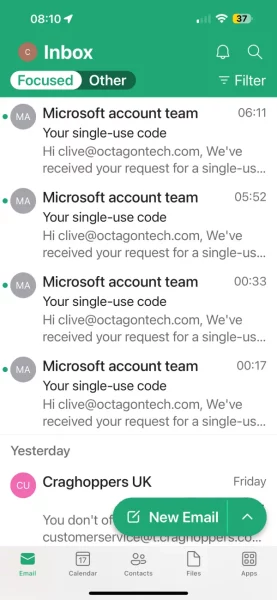
I was not going to react to the messages in any other way, except by using it as material for today’s “Wednesday Bit”.
So what was this sophisticated email phishing attack?
What I was getting were password change request codes from Microsoft, triggered by someone or something requesting them using my publicly available email address:
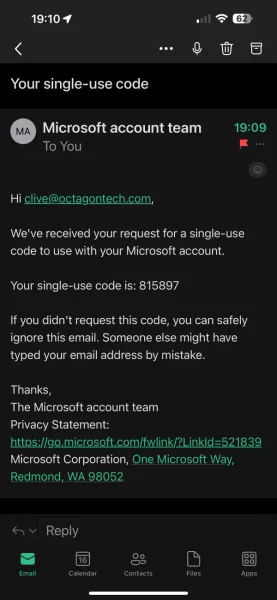
But as you can see from the email, Microsoft states that if I did not request this change, I can safely ignore the email, because the code that the hackers want has come to my email, not theirs.
So basically what you are saying is this phishing attack was useless.
Yes and no.
In our case and those of our cyber security clients, it is useless because we have a couple of cyber security defences in place for combatting this. I will share one of these with you.
For this attack to work, the hackers depend on being inside your secure perimeter, using compromised credentials that belong to one of your team and then setting up email forwarding rules to send this Microsoft email on to the hacker’s email account, whilst deleting it from the user’s inbox. One of the steps we take for our clients is to make sure no one gets more authorisation on the system than they need to do their jobs. We do not allow the existence of rogue administrators who can enable this type of email phishing attack.
Of course there is more, but as I have said before, our clients pay for that information, so I will not share it here for free.
What you need to do next?
Here is the question you need to ask yourself:
“Is our email system protected from this type of business compromise email phishing attack?”
If you do not know the answer you need to start questioning those people who might know the answer.
Clive Catton MSc (Cyber Security) – by-line and other articles
Further Reading
Bugged by Phishing Email Attacks | Smart Thinking Solutions
Bugged by Phishing Email Attacks (pt. 2) – CyberAwake
Photo by Tima Miroshnichenko



