For this week’s installment of my Phishing Email Primer, I thought it would be a good idea to show you and your teram some examples of what a phishing email looks like. But I had two problems with this.
My Phishing Email Problems
The first one was trying to find some in our email system. I operate a very high filtering level on our anti-virus/malware/email filtering systems to ensure that the threat actors have very little opportunity to get inside our systems. This gives me two headaches. It means we could find very little in our systems to illustrate what a phishing email looks like. The most dangerous emails, complete with their malicious attachments and links are simply identified and then permanently deleted.
The more serious headache is that when I sent the protection to high, certain team members were worried about false positives. They were concerned that genuine email enquiries would be deleted as false positives and that we would lose out on lucrative opportunities. This is a genuine concern and I have heard these arguments from clients when we have set up protection systems for them. In a few well-argued and considered cases we have turned down the protection from 11 to maybe 9.5 or 10. I am not going to discuss those cases here – if you need that type of advice to balance your cyber security with your business needs, then that is what our contact form is for. Our business case means that we keep the protection dialled up to 11 – even though that means no phishing email examples.
Well not quite…
My support team trolled their Outlook accounts and deep-dived into what was held by the protection systems and found a couple of examples – here they are.
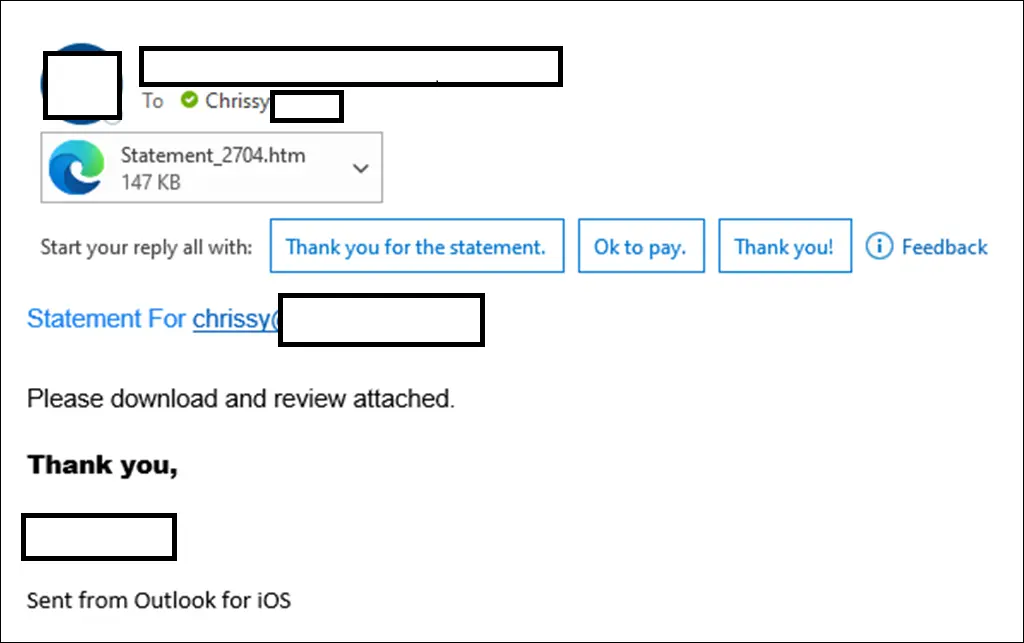
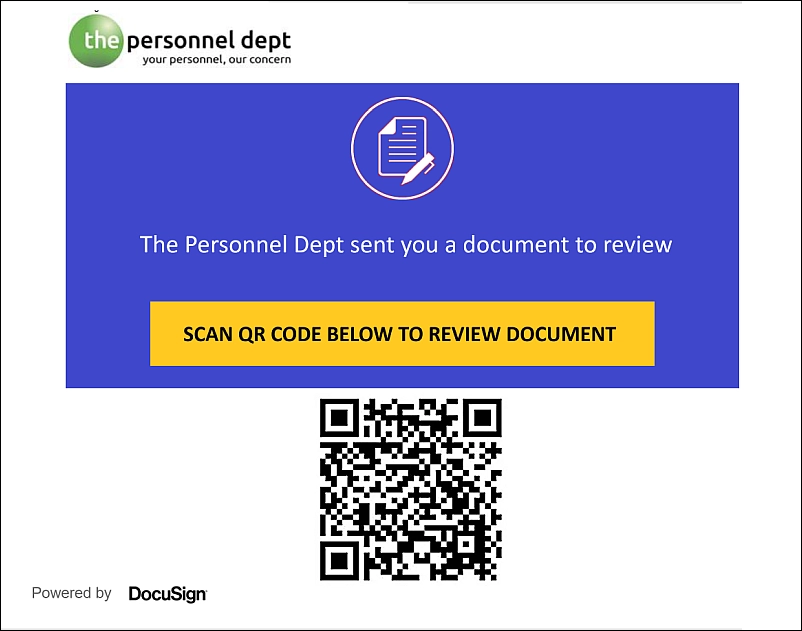
In parts 1 and 2 of this primer, we discussed social engineering as the tool to get victims to click, follow, open or even scan a malicious phishing email. You can see both of the above have a certain attraction that may cause someone to interact with the contents and set the malicious package off.
Here are examples of some phishing emails – again all including the magic spice to get you to interact. I use this slide in my Cyber Security Awareness Training.
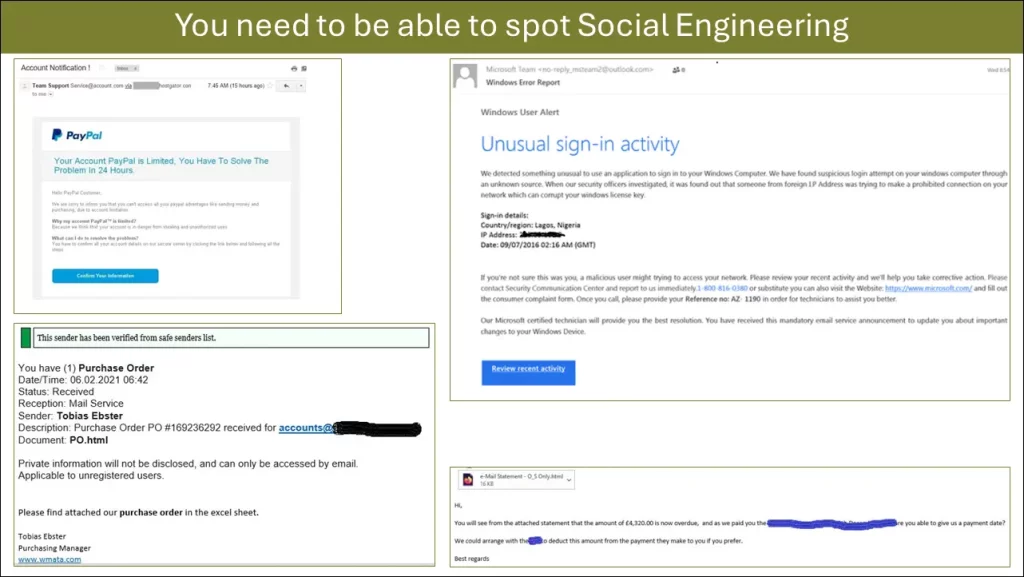
The second headache I have with showing you phishing emails…
The information above is out of date. We have discussed how AI and the availability of millions of email addresses on the Dark Web mixed with some simple OSINT are making a phishing email harder to spot both by humans and technical defences – and to me the above emails look too simple.
What do you need to know?
Recognising and reacting to phishing emails that get all the way to your comfortable safe space – the computer or device you use every day – is an ongoing process. I’ll give you two tips for combatting this menace.
1 – Regular Cyber Security Awareness Training – and do not let senior members of your team come up with excuses not to be there.
2 – Do not encourage a “blame culture” but encourage open discussion about phishing emails.
Let’s finish on a lighter note…
Some phishing emails are easier to spot!
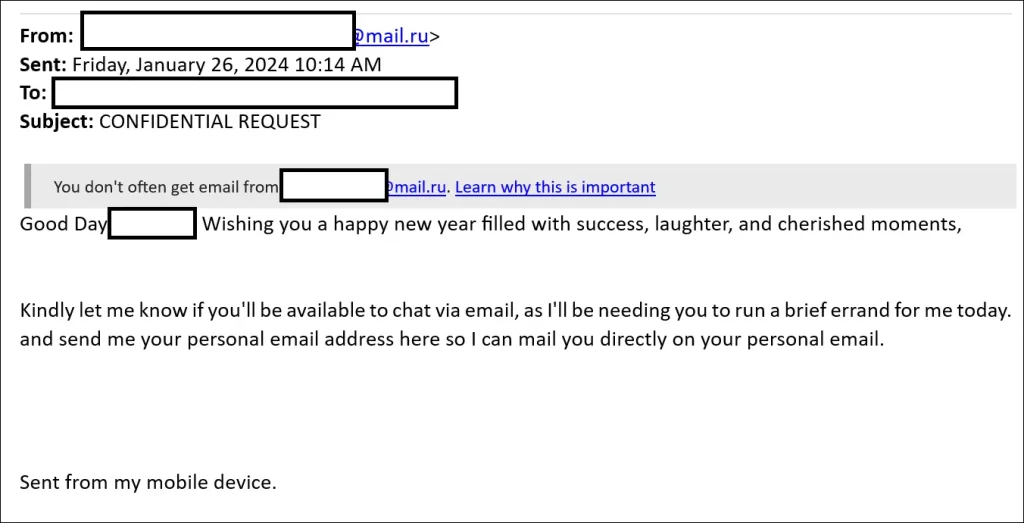
Next…
Back to bait.
Clive Catton MSc (Cyber Security) – by-line and other articles
Further Reading
Don’t Blame your Team – “Just Click Here”
Back-to-Basics Phishing Email Primer
Phishing Primer – Social Engineering (pt. 1)
Phishing Primer – Social Engineering (pt. 2)
The Phishing Email and AI (pt. 3)
Phishing Primer – Phishing Types (pt. 4)
Email phishing needs bait… (pt 5)
Phishing Attacks – It is in the numbers. (pt 6)
Nothing is true, everything is a scam (pt.7)
Photo by Tatiana Syrikova


