For a successful ransomware attack the threat actors have to get their malware onto a user’s computer inside the secure network.
Posing as your IT support is one way to get in:
Ransomware gangs pose as IT support in Microsoft Teams phishing attacks – BleepingComputer
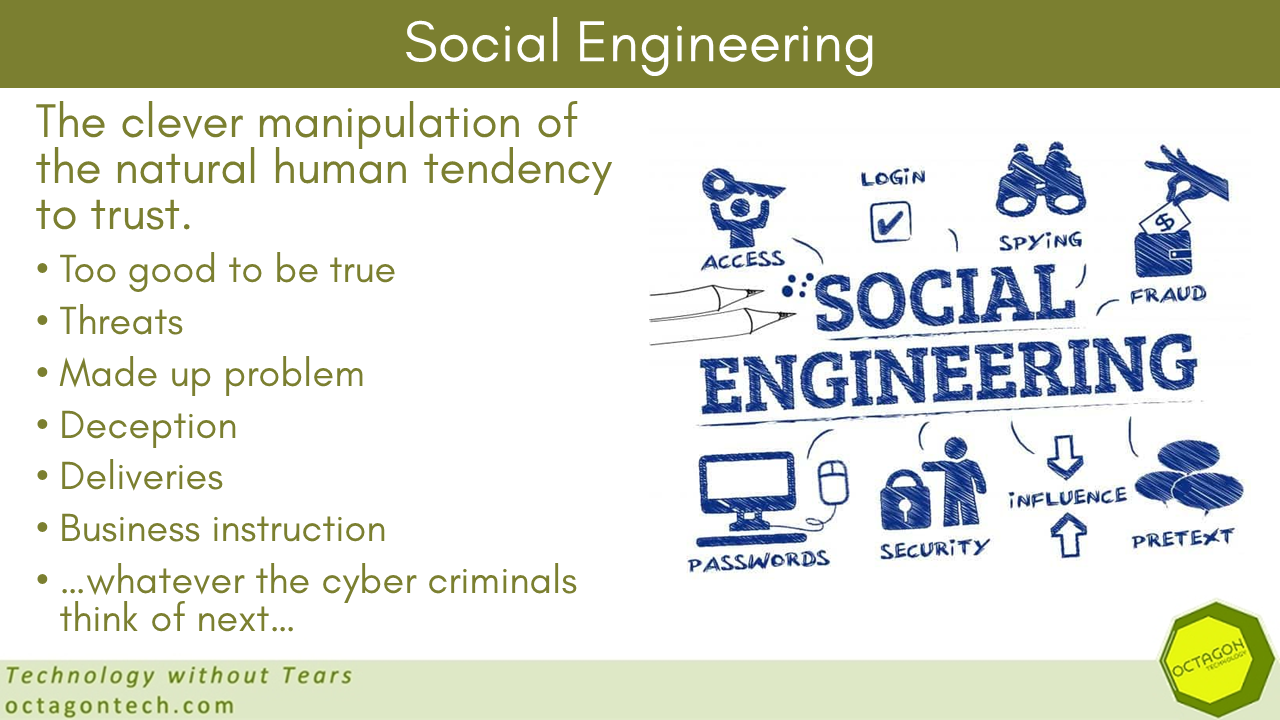
Social Engineering
In this attack the threat actors first bombard the user with thousands of emails and then contacts them offering to help fix the problem, if they would just give the hacker remote access during a Teams call. Once the remote access has been granted they can install their ransomware and take other steps to obscure the attack.
Social engineering is a key attack vector for threat actors.
Email Phishing Primer – Social Engineering (pt. 1)
Email Phishing Primer – Social Engineering (pt. 2)
Your Takeaway
There is a lot to takeaway here. Here are some questions you need to ask yourself.
- Does your team know who the IT support really is?
- Is your cyber security protection, protected from casual disruption?
- Does your cyber security awareness training include a deep dive into social engineering and how your team’s natural tendency to trust.?
One of the things we do to prove our credentials to clients is…
Well actually I’ll not write about that here as it would compromise the cyber security of all of our clients. If you want to know the process, then it is time for you to contact us.
Clive Catton MSc (Cyber Security) – by-line and other articles