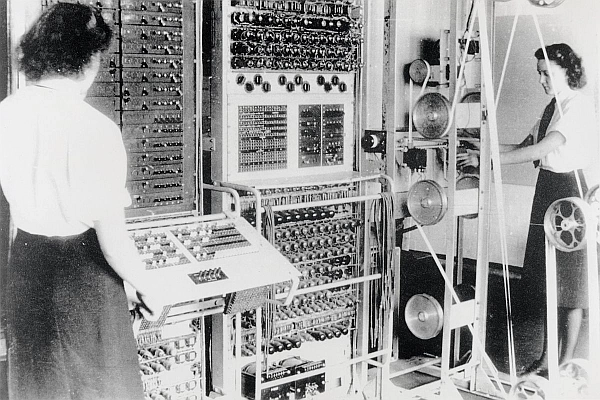
We have come a long way in cryptography and computing since the Colossus electronic computer, (above), was built at Bletchley Park, during the Second World War, to break the Lorenz cipher. With the advances in computing technology, there is a foreseeable point in the future, possibly only ten years, when …
CPU vulnerabilities – and it does not matter if you are team Intel, team AMD or team Apple!
There have been two pieces of recent research that are pointing to serious issues with a lot of the silicon we use to power our computers. Some of which may be irreparable. The Apple M1 attack is called PACMAN, as it exploits the Pointer Authentication Code (PAC). This attack bypasses …
Machine learning is vulnerable to a wide variety of attacks
This paper looks at how threat actors can manipulate and poison machine learning training, to twist the systems to their goals. The goals are achieved without impacting the integrity of the underlying data sets. Manipulating SGD with Data Ordering Attacks (arxiv.org) Shumailov, I., Shumaylov, Z., Kazhdan, D., Zhao, Y., Papernot, …
Continue reading “Machine learning is vulnerable to a wide variety of attacks”
Another example of using Bluetooth for something it was not intended for
Earlier this week, I wrote about the Bluetooth weaknesses that would allow someone to drive off with your Tesla: How to unlock a Tesla that does not belong to you! – Smart Thinking Solutions Here is a research paper, from UC San Diego, that examines how the cryptographic anonymity that …
Continue reading “Another example of using Bluetooth for something it was not intended for”
What is it about politicians and privacy?
Before we go any further Smart Thinking and Octagon Technology support any effective and legal means to protect the vulnerable and minors. Politicians, they want privacy to cloak their personal, business and political lives – but seem to hate it when private law abiding citizens want the same as them! …
Continue reading “What is it about politicians and privacy?”