For those of you who read Smart Thinking regularly, you will realise that this “Wednesday Bit” has been published a day late – the reason was a Cyber Security Awareness talk I gave yesterday at the East Lincs Expo. I delayed publishing, rather than writing an article and leaving it …
Insider Threat – How would you feel if someone betrayed your trust?
What is the Insider Threat? The insider threat is one of the most difficult cyber security issues to deal with as it involves someone you trust betraying that trust behind your back. They betray that trust and exploit the access they have to privileged information or processes. Unfortunately the insider …
Continue reading “Insider Threat – How would you feel if someone betrayed your trust?”
Credentials – A Primer
Today I am going to look at why credentials are so important in cyber security? Credentials for identity The management of credentials across your organisation for all services is an important impact of your cyber security, whether it is someone using the global administrator account as their “daily driver” work …
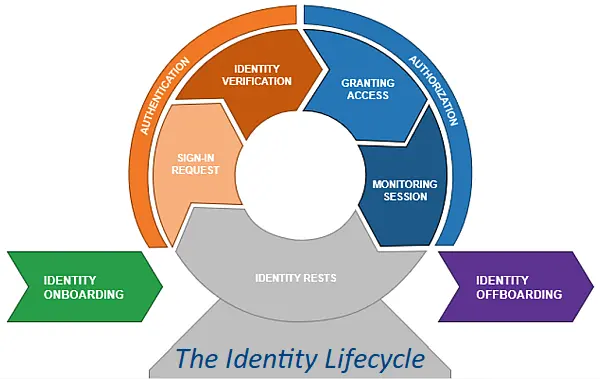
Authentication – Who Do You Let In?
Authentication, Authorisation and Accountability. This is the first part of a three-part series looking at the basics of the cyber security principle of “AAA”. Today we will start with Authentication It seems the easiest of principles. Everyone needs a username and password (credentials) to access any of your organisation’s systems. …
Because It’s Friday – A Cyber Security Joke and…
My son told me this cyber security joke, this week, as suggested material for a Because It’s Friday post. So here it is: The Cyber Security Joke I tried to use beeFsteW as a password but I was told it was not stroganoff. He’s a maths teacher! Because It’s Friday …
Continue reading “Because It’s Friday – A Cyber Security Joke and…”