Last week I had a prospective client take me up on our free 30 minute “ask me anything about your cyber security” Teams meeting. Things went well, she had some questions, I ran through my advice checklist with her – everyone was happy until I asked about their anti-virus – …
Deepfake
The stakes can be high when threat actors invest the time and money into creating deepfake videos to hack an organisation, here an example from last year: You may not have $25m in your bank account but here is the state of play of deepfake hacking So tools that can …
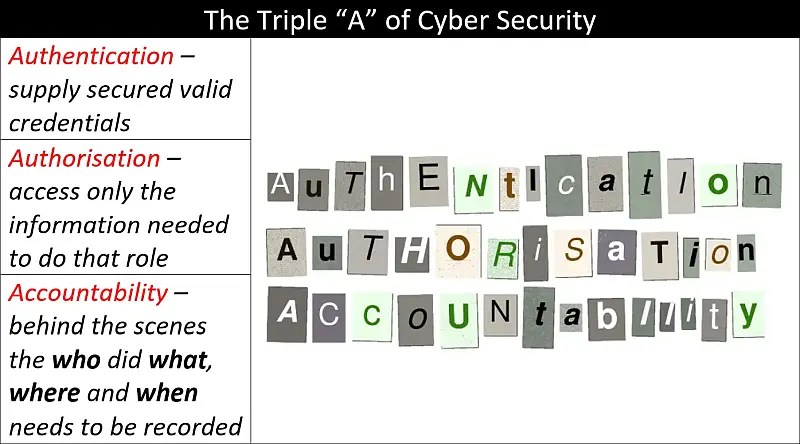
Authentication, Authorisation and Accountability – A Primer
Authentication, Authorisation and Accountability (AAA) and The Principle of Least Privilege (PoLP) come together in this primer to give you a basic understanding of the importance of knowing who is accessing your information and how much they can access. Another important idea covered here is what happens when something goes …
Continue reading “Authentication, Authorisation and Accountability – A Primer”
To Catch A Thief… A Story of a Security Operations Centre
I am sorry, the title is a bit misleading, but once you have read the article, I am sure you will see how we – and the Security Operations Centre – could have caught a thief. Additionally, it is not about the Hitchcock movie; however, some of the action does …
Continue reading “To Catch A Thief… A Story of a Security Operations Centre”
Delivery Scam – follow up
No, not an explanation from Evri or AliExpress – not that I expected one from either of them following this article: But a useful advice article from the Google blog: Google shares tips to avoid email, phone, text and Search scams Your Takeaway Two things. Photo by Tara Winstead